.png?width=713&name=OhNo-I-clicked-2%20(1).png) It's just a fact of life: If there's email, there will always be spam. Now, how much spam you have to deal with will depend on how good your spam filtering solution is. Here at MDaemon Technologies, we use our own products - MDaemon and Security Gateway, to filter out spam, malware, phishing attempts, and all of the other junk that often floods inboxes of users whose email server or hosted service isn't as effective.
It's just a fact of life: If there's email, there will always be spam. Now, how much spam you have to deal with will depend on how good your spam filtering solution is. Here at MDaemon Technologies, we use our own products - MDaemon and Security Gateway, to filter out spam, malware, phishing attempts, and all of the other junk that often floods inboxes of users whose email server or hosted service isn't as effective.
"If I have a good spam filter, do I REALLY need to know how to recognize phishing scams?"
If an email security company or hosted provider tells you their spam filter will catch 100% of spam, they're not being completely honest. Most companies say their products catch 99% or 99.5% in their SLA (Service Level Agreement), with a false-positive rate of %.0001 or less. That's reasonable and to be expected, especially considering the statistics.
According to public data, spam made up over 71% of global email traffic in April, 2014. As of September, 2018, spam volume had decreased to 54%, but considering that over 281 billion email messages are sent per day worldwide, that's still over 151 billion spam messages sent every day, and while spam may be decreasing in total volume, it's becoming more dangerous, with cryptojacking overtaking ransomware as the attack vector of choice for cybercriminals, and malware-as-a service turning cybercrime into a commodity for the masses,
So no matter how good an email security product is, there is always that chance that new and emerging (and sometimes tried-and true) social engineering techniques will succeed in tricking the next unsuspecting victim to part ways with his or her company's bank account details.
And that brings me to the point of today's post. It bears repeating that companies of all sizes and industries should consider ongoing training with their employees on how to recognize phishing attempts.
In today's example, the scammer is using a classic BEC (Business Email Compromise) attack to try to get the recipient to open a malicious ISO file.
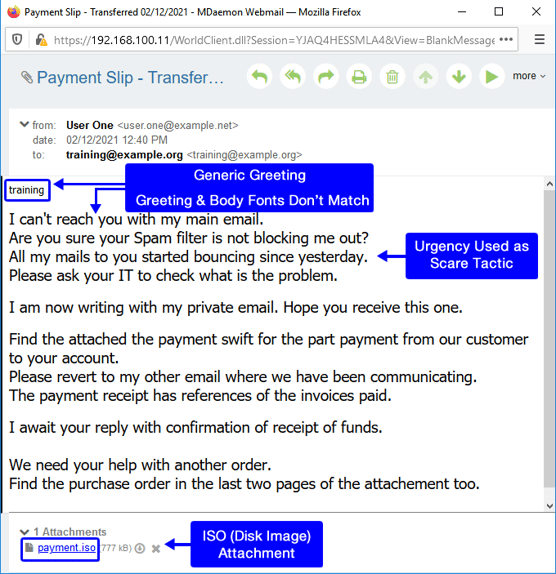 Phishing email using common Business Email Compromise tactics
Phishing email using common Business Email Compromise tactics
Because the threat of phishing and Business Email Compromise will continue well into the future, I will revisit this topic regularly throughout the year.
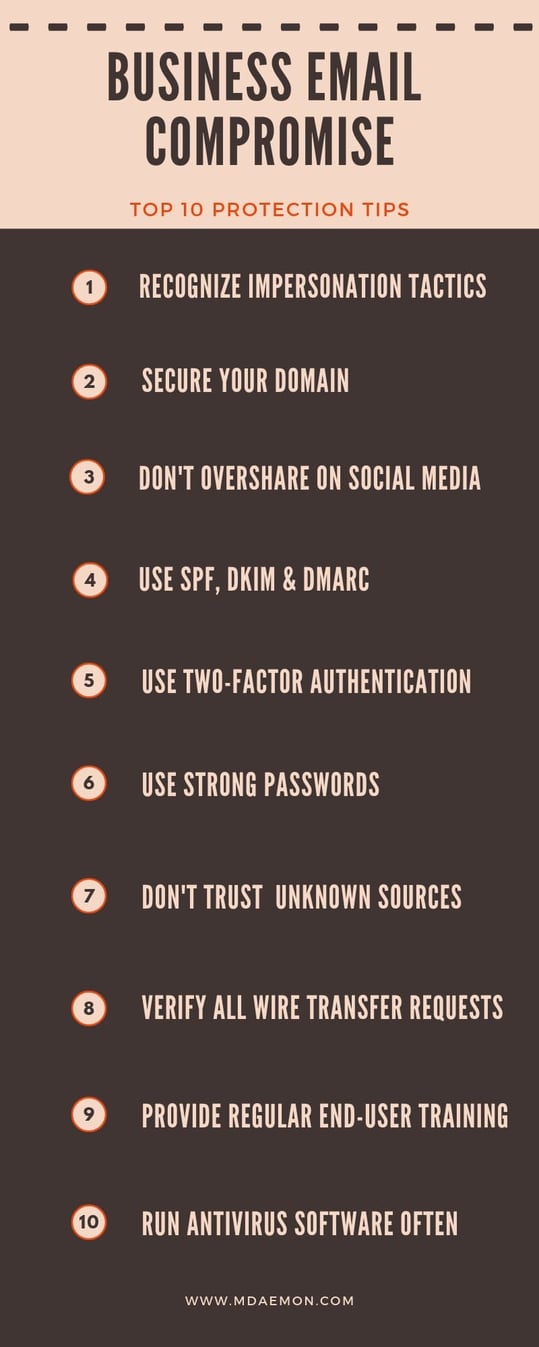
Meanwhile, I would recommend sharing with all employees and business executives these 10 best practices for avoiding common email scams.