
In part one of our three-part series on Business Email Compromise (BEC), I explained what a BEC attack is and provided examples and statistics. As you’ll recall from the examples discussed, businesses have suffered staggering losses to these attacks, and while users are becoming more aware of them, their own human nature dictates that these threats will continue. In fact, a recent report by Get Safe Online indicated that over a third (37%) of employees don’t know what to look for to identify common email scams. The report also stated that one in 20 email fraud victims were so ashamed that they hid their mistakes from their colleagues.
In part two, I discussed the following 4 steps cybercriminals take to conduct a BEC attack.
- Identify the target victim
- Grooming
- Exchange of information
- Payment
Businesses can make Step 1 more difficult by carefully crafting and monitoring online content such as company websites, LinkedIn profiles and other publicly available information, but as long as employees can be influenced by excessive trust, intimidation, or simply lack of awareness, businesses will need to implement additional preventive measures to avoid potentially devastating losses. After all, once a credible target has been identified, the best defense is a well-informed workforce.
Top 10 Business Email Compromise Protection Tips
-
Train Users to recognize these Common Impersonation Tactics used by Cybercriminals
Domain Name Spoofing – Domain name spoofing involves either spoofing the sender’s “Mail From” to match the recipient's domain in the message envelope, or using a legitimate domain in the “Mail From” value but using a spoofed “Reply-To” domain in the message header.
Here is an example that has been spoofed to look like it was sent from HSBC Bank:
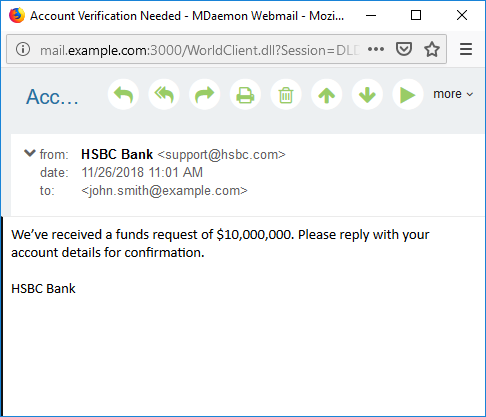
A quick examination of the message headers reveals a return-path address that is not associated with the From address. A reply to this message would go to frank.thomas@example.com.
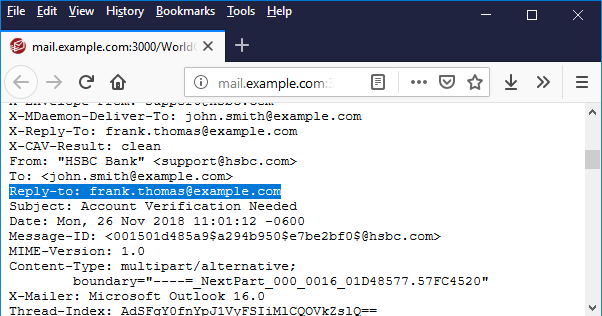
Display Name Spoofing – Most BEC attacks use this technique. With display name spoofing, the attacker will register a free email account that may contain the name of a company executive. The attacker would then configure the display name to match your CEO or some other executive, and then send phishing messages from this account. This technique works because recipients often only look at the display name and not the actual email address. In fact, many email clients (particularly on mobile devices) will only show the display name when viewing the message, making it easier to hide the sender's real identity. Because the sender's email address is not forged, messages using this spoofing technique are often more difficult to block than those using domain name spoofing, where the addition of three DNS records (DKIM, SPF and DMARC) have been shown to be more effective at blocking spoofed emails.
Here is an example showing a spoofed display name of HSBC Bank. To help users identify suspect emails, MDaemon Webmail has a handy security feature that displays the actual sender address as well as the display name.
 Display Name Spoofing
Display Name Spoofing
Lookalike Domain Spoofing – Lookalike domain name spoofing involves registering fake domains that contain characters that look similar to others and sending phishing emails from them in an attempt to trick the recipient into thinking the message is from a legitimate domain. An example would be using an upper-case I in place of a lower-case L.
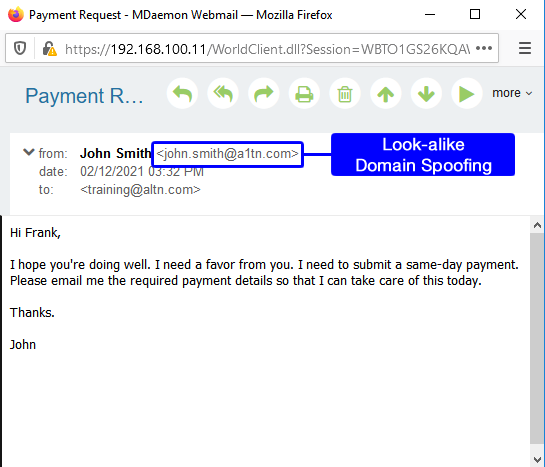 Business Email Compromise email using lookalike domain
Business Email Compromise email using lookalike domain
Compromised Email Account – Another common tactic is the use of legitimate email accounts that have been compromised through malware or social engineering to steal data or funds.
-
Secure your domain
Register domain names similar to yours to protect against lookalike domain spoofing.
-
Don’t over-share on social media
Be careful what you post on social media, especially job titles and responsibilities, corporate structure information, and out-of-office details.
-
Use SPF, DKIM and DMARC
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting & Conformance (DMARC) are anti-spoofing and email authentication techniques that use DNS records to validate the sender of an email. Make sure your domain has valid SPF, DKIM and DMARC records, and make sure your mail server/provider is analyzing all inbound email traffic using these tools. For more information, refer to this blog post.
-
Use two-factor authentication
With two-factor authentication, users must provide two forms of authentication – a password and another form of verification such as a unique verification code or a fingerprint. Two-factor authentication is discussed further in this blog post.
-
Use strong password policies
Use strong passwords and require regular password changes. Strong passwords must meet the following criteria:
- Must meet a minimum length requirement.
- Must contain both letters and numbers.
- Must contain both upper and lower case letters.
- May not contain the account mailbox or full name data.
- Never use commonly guessed passwords such as Password1 or Letmein.
-
Don’t trust unknown sources
Never open emails, click on links, or download files from unknown senders. To help users verify the identity of a message sender, MDaemon Webmail displays the full email header in addition to the display name.
-
Establish strict processes for wire transfers
You may recall from my previous post that cybercriminals have been known to target all parties in a real estate transaction. If you receive a request to change the payment type or the original recipient’s financial information, be sure to verify the information through already-established channels of communication.
Before responding to wire transfer requests, verify the identity of approved vendors and the authenticity of their invoices. Confirm in person or by phone using previously known numbers. Don’t trust the phone number on the invoice.
-
Provide regular end-user training
User education must be reinforced on a regular basis for stronger awareness. Every employee who uses email should know how to recognize a spoofed email or a phishing attempt.
-
Run antivirus software often
Make sure your antivirus software is up-to-date and run it regularly.
While traditional security measures such as network defenses and email gateways can be effective at blocking most varieties of spam, the bottom line is that user awareness and education are critical to avoid falling victim to BEC attacks.


