As long as healthcare organizations continue to use email, cybercriminals will find new ways to exploit security gaps, software bugs, and basic human nature to extort millions of dollars from their victims. In just the first six months of this year, Becker’s Hospital Review has noted more than 65 separate incidents of malware, ransomware and phishing attacks on healthcare providers, ranging from Alaska and Hawaii to Florida and Maine. These attacks affected more than 1.14 million patient records in just the cases that released statistics; the true number of those affected is much higher. While one-third of these attacks are specifically noted as being email-related, again, the true number is likely much higher.
.jpg?width=713&name=Security%20concept%20Lock%20on%20digital%20screen%2c%20illustration-1%20(1).jpg)
All this begs the question: Is your healthcare facility doing absolutely everything possible to guarantee the security of your email systems? Across the business landscape, reports show that over 29% of businesses saw their Office 365 accounts compromised in a single month last year. That’s why you need the additional protection offered by Security Gateway for Email Servers to protect against email-borne threats.
Here are our top 15 recommendations to protect your business from email-borne threats with Security Gateway
Security Gateway was designed to be easy to use while providing the strongest protection against spam, phishing and data leaks. While most security settings are configured for optimal protection by default, here are our top 15 recommendations to protect your healthcare facility from email-borne threats with Security Gateway.
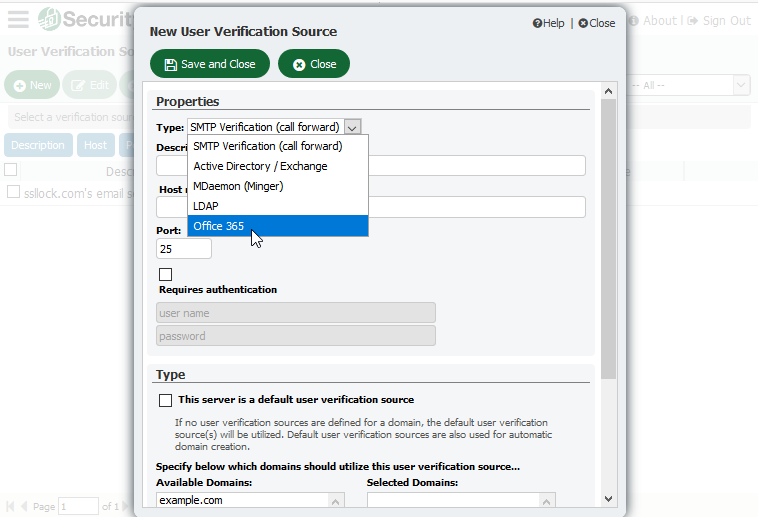
1. Verify That a User is Valid Before Creating an Account
With every incoming message addressed to an unknown local user, Security Gateway needs to be able to verify that the account is a valid local user by querying Office 365, Active Directory, MDaemon or another data source before creating the account and delivering the message. We recommend using one the five user verification sources found in Security Gateway to validate accounts.
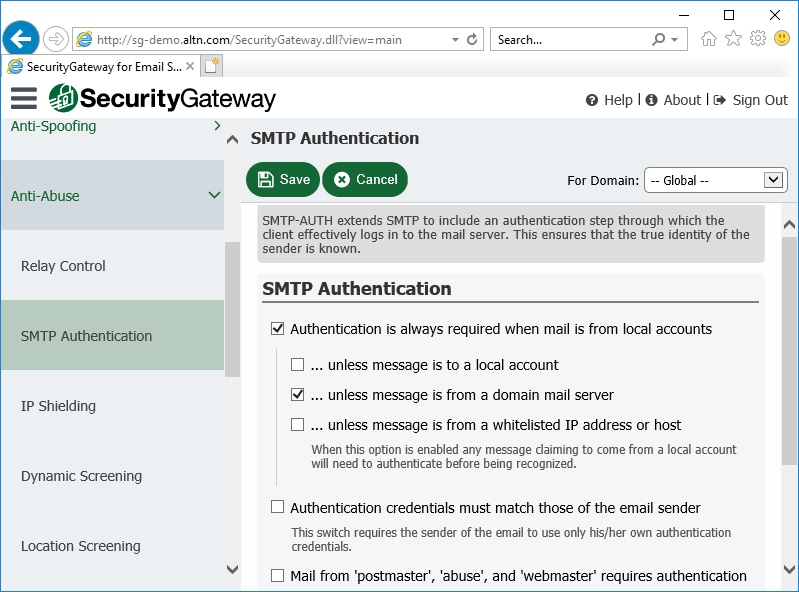
2. Use SMTP Authentication to Prevent Unauthorized Account Access
To help prevent unauthorized account access, we recommend requiring SMTP authentication unless a message is transmitted from a domain mail server.
3. Use Strong Passwords
Spammers will often try to hijack an email account by guessing its password. Therefore, passwords that are easy to guess should always be avoided. If Security Gateway is configured to create accounts automatically by querying a user verification source, then make sure your user verification source is configured to require strong passwords. Passwords can also be assigned to users manually via the Domains and Users menu.
Tip: If you are using MDaemon as your mail server, we’ve added a new security feature that will check all user passwords against a third-party list of compromised passwords that have appeared in a data breach. Also, here’s more information on configuring MDaemon to require strong passwords.
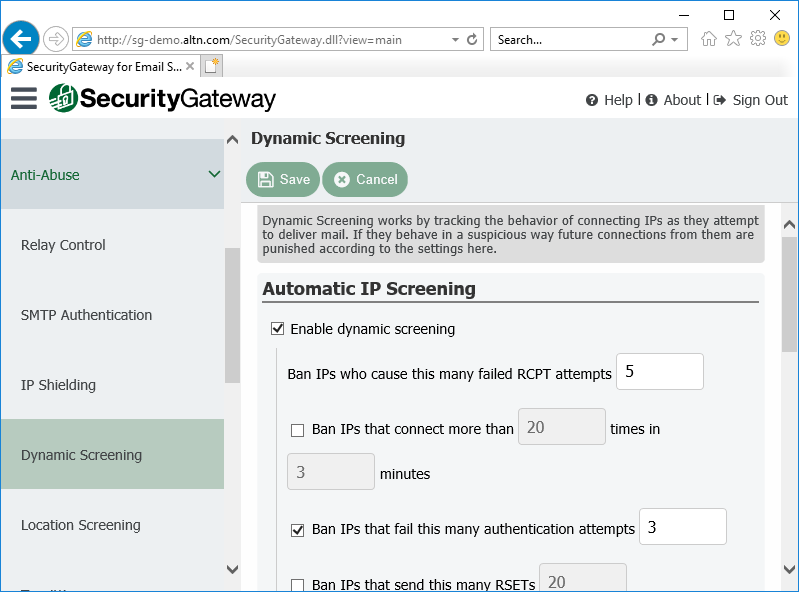
4. Enable Dynamic Screening
Enable Dynamic Screening blocks connections that exhibit suspicious activity, such as failing too many authentication attempts, connecting too many times in a given time frame, attempting to keep a connection open too long, or sending to too many invalid recipients. Dynamic screening makes it more difficult for a malicious person to guess passwords by detecting the malicious activity and blocking the connections.
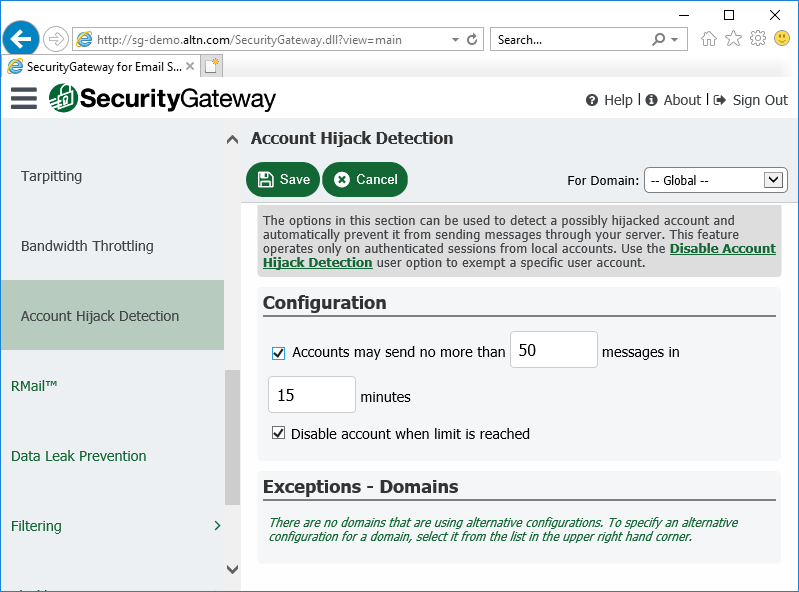
5. Enable Account Hijack Detection
If a spammer guesses an account’s password, he can then use that account to send out spam. To limit the spammer’s ability to abuse a compromised account, enable account hijack detection and then enter the maximum number of messages that can be sent in a given time frame. Once the limit has been reached, the account is disabled and the administrator is notified.
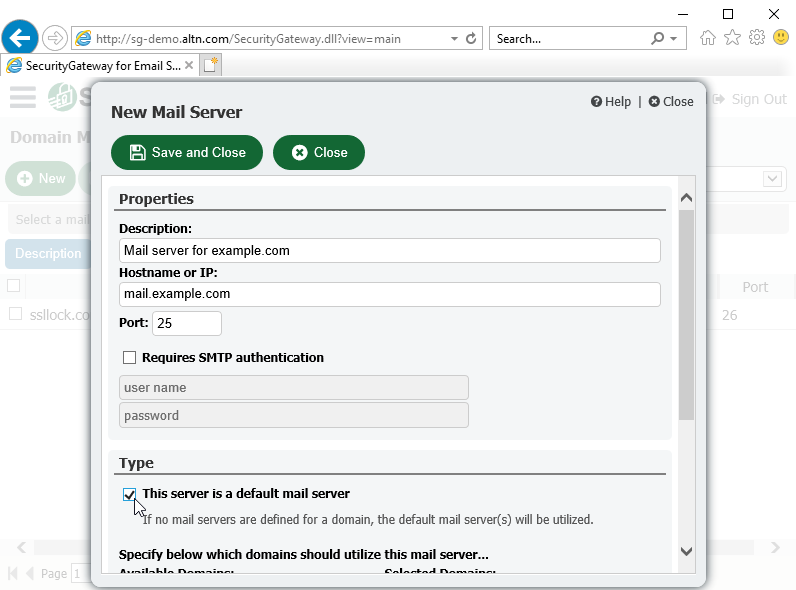
6. Enable at Least One Default Mail Server
When email arrives for a domain that has not been assigned its own mail server, Security Gateway needs to know where to send those messages. We recommend adding a default mail server for all Security Gateway domains that have not had domain mail servers specifically associated with them.
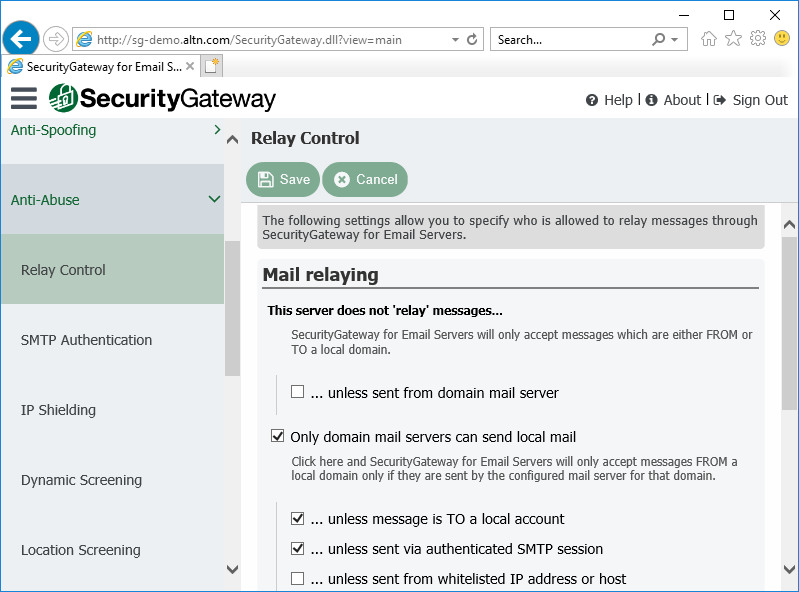
7. Prevent Unauthorized Mail Relaying
Relaying occurs when mail that is neither to nor from a local account is sent through your server. Servers that are not properly configured to prevent relaying can end up on a blacklist. By default, Security Gateway does not allow mail relaying.
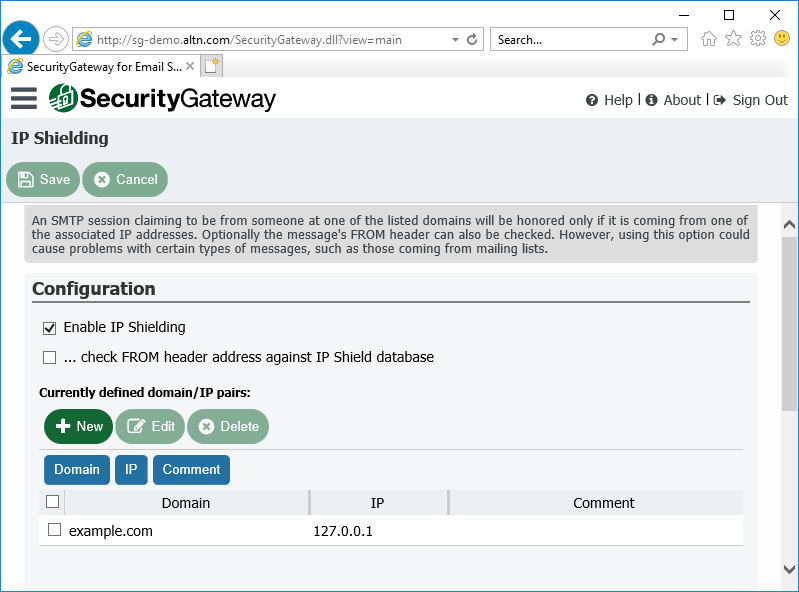
8. Protect Your Domain with IP Shielding
IP Shielding is a security feature that only honors SMTP sessions claiming to be from someone at one of the listed domains if they are coming from an IP address associated with that domain.
The best way to secure outbound email is via SMTP authentication. However, for businesses that need to send email from a printer or other device that is not capable of authenticating, IP Shielding can be used to exclude certain IP’s or ranges from having to authenticate. Messages from authenticated sessions can optionally be exempt from IP shielding requirements.
9. Enable SSL to Ensure Data Privacy
To protect the privacy of transmitted data, we recommend enabling the SSL encryption features for SMTP and HTTP.
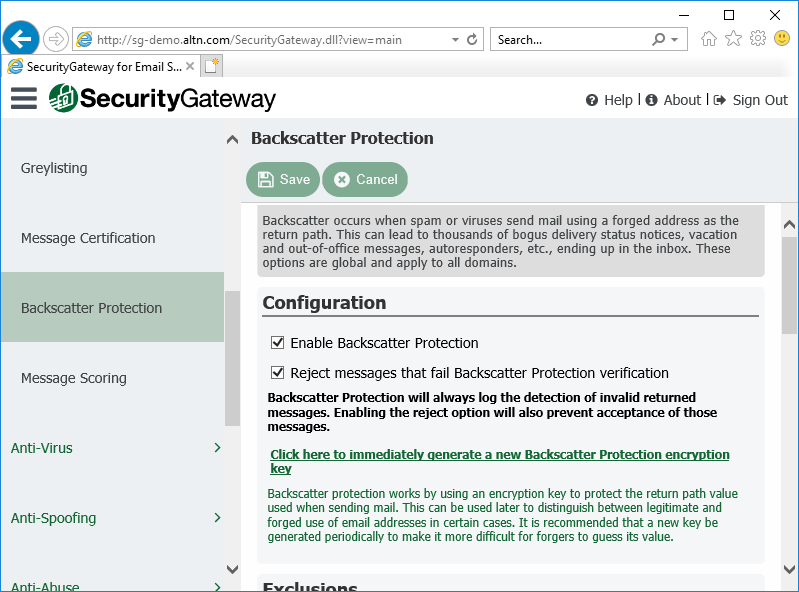
10. Enable Backscatter Protection
Most spam messages contain a forged return path. This often leads to users receiving thousands of delivery status notices, auto-responders and other messages in response to messages that the user never sent. This is known as backscatter. To combat it, Security Gateway’s Backscatter Protection feature can help to ensure that only legitimate Delivery Status Notifications and auto-responders get delivered to your domains.
11. Don’t Whitelist Local Email Addresses
In many cases, local IP addresses or host names may need to be whitelisted. However, we do not recommend whitelisting local email addresses. If a local address is added to the whitelist, messages sent to this address could bypass many of your security settings and put your server at risk of being blacklisted.
12. Protect Your Email Infrastructure from Virus and Spam Outbreaks
Security Gateway scans all inbound and outbound mail using the Cyren and ClamAV antivirus engines. It also includes Cyren Outbreak Protection, which is real-time anti-spam and antivirus technology that is capable of proactively protecting your email infrastructure automatically and within minutes of an outbreak.
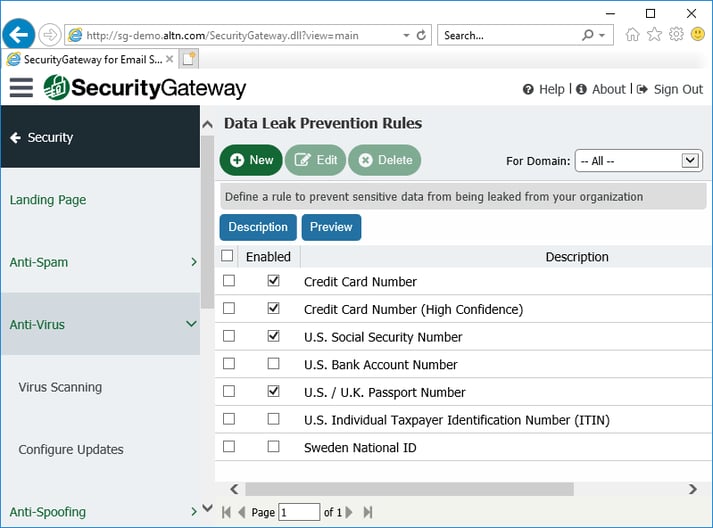
13. Prevent Data Leaks
Security Gateway includes over 70 Data Leak Prevention rules to help prevent unauthorized transmission of sensitive information such as personal identification numbers, credit card numbers and other types of confidential data. These rules can be configured to send messages containing sensitive content to the administrative quarantine for further review, redirect the message to a designated address, or encrypt the message.
We recommend enabling the appropriate Data Leak Prevention rules to suit the needs of your specific healthcare organization.
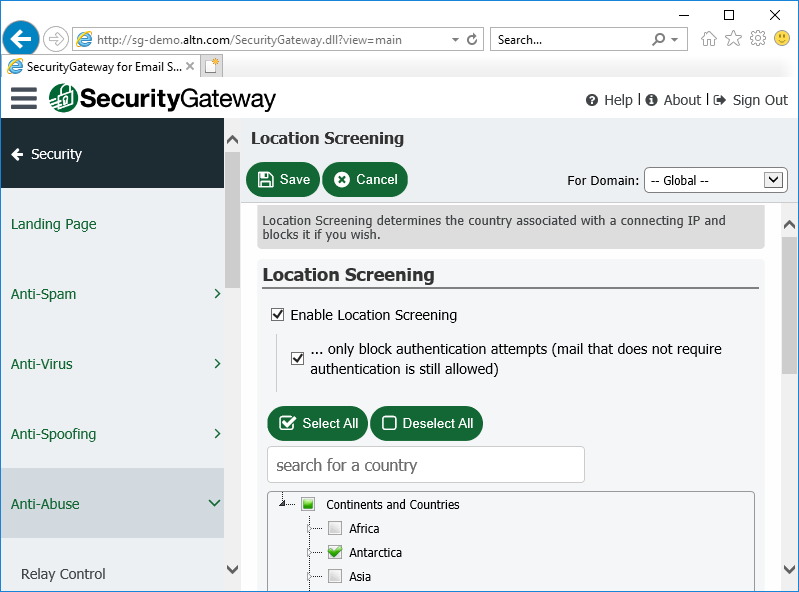
14. Enable Location Screening
Use Location Screening to block inbound SMTP and HTTP connections from unauthorized countries. If your company has no legitimate business need to communicate with a particular country, then refusing connections from that country can potentially block large amounts of spam. Alternatively, you can configure Location Screening to only prevent authentication from unauthorized countries.
15. Enable Macro Detection in Microsoft Office Documents
Cyber Criminals often use macros in email attachments to spread malware. In Security Gateway 6.5 and up, the virus scanning settings include an option to detect macros in Microsoft Office documents and flag them as infected. Security Gateway can refuse these messages or quarantine them for administrative review.
Would you like to learn more about how Security Gateway for Email can help protect your healthcare facility and its data? Visit SecurityGatewayForEmail.com to sign up for hosted or on-premise email protection.