Online scams are nothing new -- but as email has evolved and improved, so have scammers and the messages they send. Nefarious emails, attachments and links now appear sophisticated and look legitimate, sometimes tricking even the most meticulous user.

Billions Lost to Business Email Compromise
Referred to as the “Billion Dollar Scam” by the Federal Bureau of Investigation, a very specific type of scam known as the Business Email Compromise (BEC) claimed over 19,000 victims in 2020 alone, at a total annual loss of over $1.8 billion. And while law enforcement agencies have made multiple arrests in their efforts to crack down on BEC threats, cyber gangs continue to launch BEC attacks at increasing rates. For example, before 11 members of the CyberTerrier BEC gang were arrested, the hacking group still managed to steal over 800,000 usernames and passwords, which could be used to hack into accounts and use them to target more businesses.
Businesses must be aware of BEC scams, which have many variations and could result in substantial loss of money or data security, or a damaged reputation.
Four Reasons BEC Scams Work So Well
BEC emails are advanced phishing scams, and they’re on the rise. But what makes a BEC attack so dangerous, and so effective?
BEC Scams Are Highly Targeted
These scammers aren’t blasting thousands of the same email. They’ve done the research, monitoring the company’s website and social pages. They sidestep basic security strategies such as email filtering by finding only the most appropriate targets and grooming them by sending multiple conversational emails.
They Contain No Malware
Unlike the old style of phishing where users are told to click on a link, BEC emails have no spammy links. This means they can sometimes evade spam filters, and the end user doesn’t see any red flags.
They Exploit Human Nature
BEC emails carefully impersonate an actual person, complete with authentic-looking email addresses, formatting, company names, and titles. The victim has unknowingly been emailing back and forth with the scammer and comes to trust they are who they claim to be. So when asked to send bank information, for example, the victim assumes the request is authentic and complies.
They Are Often Under-reported
Victims often don’t realize they made a mistake until much later. Even upon realization, many companies don’t report the incident for fear of damaging their reputation with their customers. Not reporting such incidents allows perpetrators to simply move on to their next victim.
Learn How to Protect Against BEC Scams
 Top 10 Business Email Compromise Protection Tips
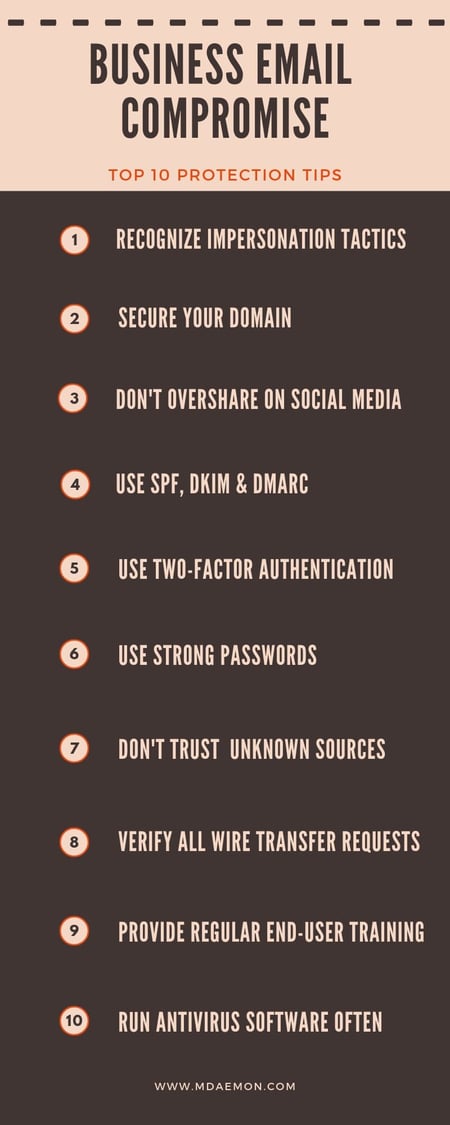
Top 10 Business Email Compromise Protection Tips
Preventing losses due to Business Email Compromise is the responsibility of all of your employees as well as your IT administrator. To stay protected, follow these tips:
End Users:
- Double-check the sender email address and know how to recognize spoofing and other impersonation tactics. MDaemon Webmail displays the full email header to help users identify spoofed emails.
- Don’t overshare on social media
- Don’t open email from unknown sources
- Verify all wire transfer requests via phone or face-to-face
- Know customers’ and vendors’ business practices
- Run antivirus software often
- Use two-factor authentication
- Forward, don’t reply; this ensures you manually enter the appropriate email address
Administrators:
- Enable reverse lookups to verify the legitimacy of the sender
- Use the antivirus features in MDaemon and SecurityGateway to scan all inbound and outbound email traffic for malware
- Require users to use SMTP authentication
- Use SPF, DKIM & DMARC to secure your domain against spoofing
- Require two-factor authentication
- Require strong passwords
- Provide regular end-user training on all scam formats including BEC
- Run antivirus software often and make sure virus signatures are up-to-date
While traditional security measures such as network defenses and secure email gateways can be effective at blocking most varieties of spam, the bottom line is that the most critical part of stopping BEC attacks is user awareness and education. Take steps to protect your business and its data today. Visit SecurityGatewayForEmail.com to sign up for hosted or on-premise email protection.


