The COVID-19 pandemic’s global spread has paved the way for threat actors to unleash the most widely-used cyber threat in recent memory. And healthcare entities are the most frequent target.

Hackers are taking advantage of the current healthcare crisis through ransomware and misinformation campaigns, COVID-19 hoax websites, and email scams, according to a 4iQ report in June. At the same time, ForgeRock released its annual consumer identity breach report, which found that healthcare was the most targeted sector in 2019, with the average cost of a single breach increasing 112% to $8.9 million. In addition, the number of breaches impacting consumers rose 79% to 5 billion in 2019. The most common type of breach? Unauthorized access, accounting for 40% of incidents.
Preying on Fear
At the heart of these threats is a disinformation campaign that is spreading as rapidly as the coronavirus itself. Scammers know people are looking for answers and are more likely to click on embedded links in email messages or download malicious email attachments during moments of heightened concern. Healthcare employees are no less likely than the general population to be affected by these concerns, making your employees an attractive target to scammers -- particularly if your employees are working from home.
Thousands of COVID-19 related email scams and malicious sites are being created on a daily basis. In just a few recent examples cited by Health IT Security,
- The CoronaVirus ransomware variant infects victims’ computers through a Windows utility and is distributed through a fake website masquerading as system optimization software and utilities.
- The REvil or Sodinokibi ransomware variant has predominantly targeted the healthcare sector through attempted exploits on virtual private networks and other remote gateways.
- Ryuk and Locky ransomware hacking groups have also targeted the healthcare sector throughout the pandemic through targeted phishing campaigns.
And as long as the coronavirus poses a threat, cybercriminals will continue their attempts to exploit individual fears for personal gain. That’s why it’s even more important to help your healthcare employees learn to identify potential threats such as email spoofing, spear phishing scams, phone scams, and other social engineering tricks.
What’s being done to Protect the Public from COVID-19 Scams?
Facebook, Twitter and Google are cracking down on misinformation regarding the Coronavirus pandemic. Facebook has said it would start taking down bogus claims about purported cures and other misleading content. To help users cut through the steady stream of misinformation, they’ve created a helpful resources page, with tips on avoiding COVID-19 scams.
Twitter users can find helpful information on their blog.
Google has also stepped up efforts to direct users to verified sources on the Coronavirus.
Even the FTC and FDA have stepped in to protect people from mis-branded or unapproved products such as essential oils and teas.
Tips to avoid email related phishing scams
Cyber Criminals will continue to use social engineering and scare tactics to trick your employees into opening malicious attachments or supplying personal information. Take the time to review best practices for avoiding spear phishing attacks and other social engineering scams, including:
- Always double-check the sender address in an email: never trust the display name shown in your email client, as this can easily be spoofed. The From header can also be spoofed, as shown in this example.
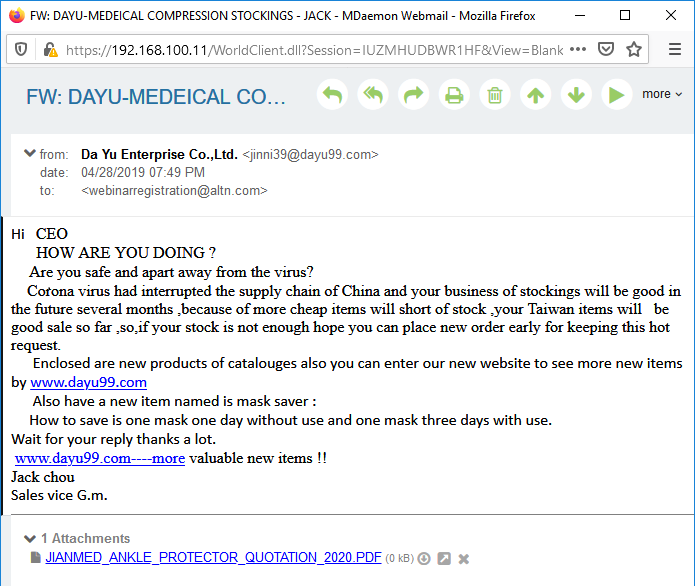
- Never click on links without proper verification. When in doubt, manually type the URL in your browser.
- Be aware of the privacy policies of the Centers for Disease Control (CDC) and World Health Organization (WHO). These and other reputable organizations have strict communication policies to protect people from scammers impersonating them.
Businesses can promote online privacy and help protect remote workers from phishing and malicious email threats
The surge of employees working from home during this crisis brings additional cyber security challenges. Your healthcare data security teams should ensure these challenges are met with secure VPNs, strong password policies, and fully-patched systems.
Seven Email Security Tips for MDaemon and Security Gateway Users
While end-user training and awareness are important, the IT administrators at your healthcare facility play a significant role in protecting your employees against phishing email scams. Both MDaemon Email Server and Security Gateway for Email have features designed to block spam, spear-phishing, and malware attacks, so when considering best practices for providing the most secure email solution for your facility, we recommend following these best practices.
1. Use SMTP authentication to prevent unauthorized account access
To help prevent unauthorized access to local email accounts, we recommend requiring SMTP Authentication unless a message is transmitted from a domain mail server. This helps to ensure that the identity of the sender is valid. Instructions for configuring SMTP authentication settings in Security Gateway can be found here in our knowledge base. Click here to read how to configure SMTP authentication in MDaemon Email Server.
2. Use strong passwords
Spammers will often try to hijack an email account by guessing its password. Therefore, passwords that are easy to guess should always be avoided.
3. Ensure domain email is from an authorized email client.
Both MDaemon and Security Gateway have a security feature called IP Shielding that helps protect against spoofing by accepting email from a local domain only if it was sent from an IP address associated with that domain.
We always recommend using SMTP authentication when sending outbound email. However, for healthcare facilities that need to send email from a printer or other device that is not capable of authenticating, IP Shielding can be used to validate the sender. With IP Shielding enabled, email from a local address is only accepted if it was sent from an authorized IP address (such as a client or device on your local network). Messages from authenticated sessions can optionally be exempt from IP Shielding requirements.
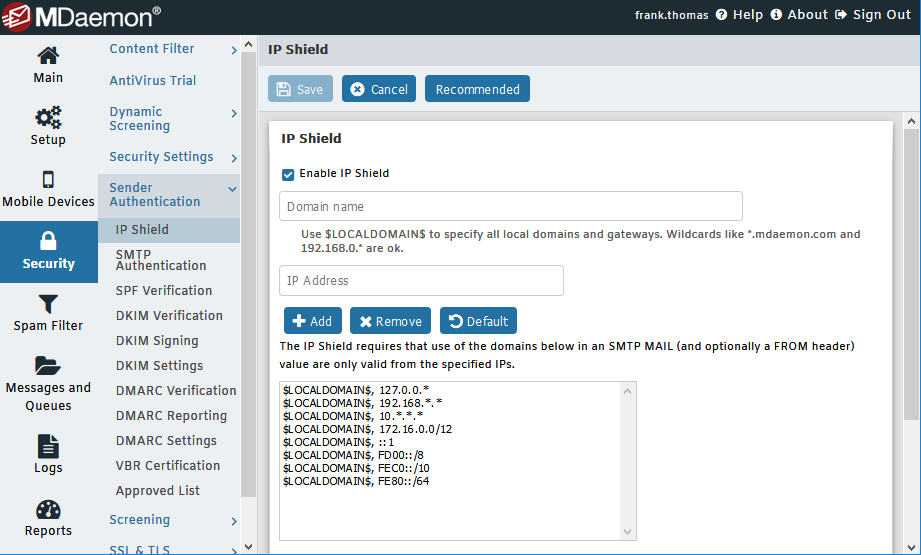
Instructions for configuring IP Shielding can be found here:
4. Don’t whitelist local email addresses
In some cases, local IP addresses or host names may need to be whitelisted to bypass certain email security features. However, we do not recommend whitelisting local email addresses. If a local address is added to the whitelist, messages sent to this address could bypass many of your security settings and put your mail server at risk of being blacklisted.
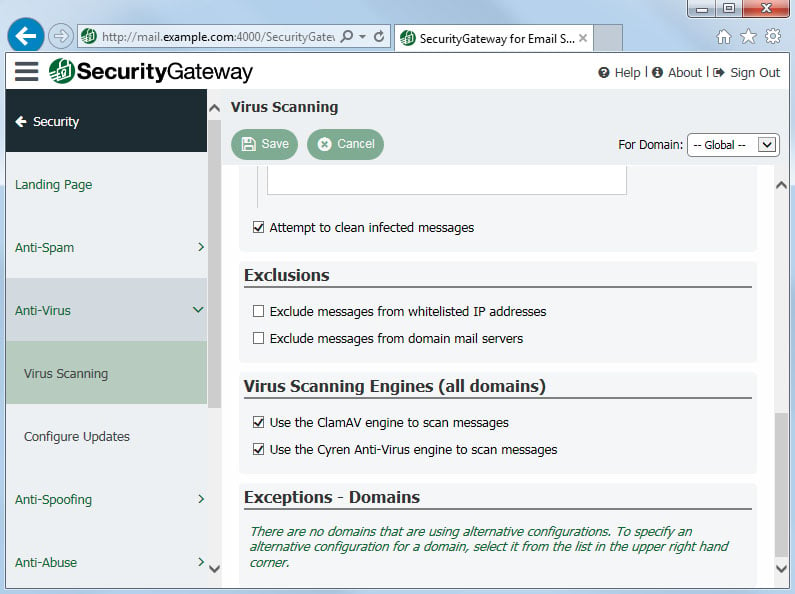
5. Protect your email server from virus and spam outbreaks
Whether you use MDaemon Email Server or Security Gateway for Email, we recommend enabling the antivirus features to scan all inbound and outbound email messages for viruses. Security Gateway uses the Cyren and ClamAV antivirus engines to scan messages for viruses and malware, and to detect the latest spam outbreaks. For MDaemon, these features are available with MDaemon AntiVirus.
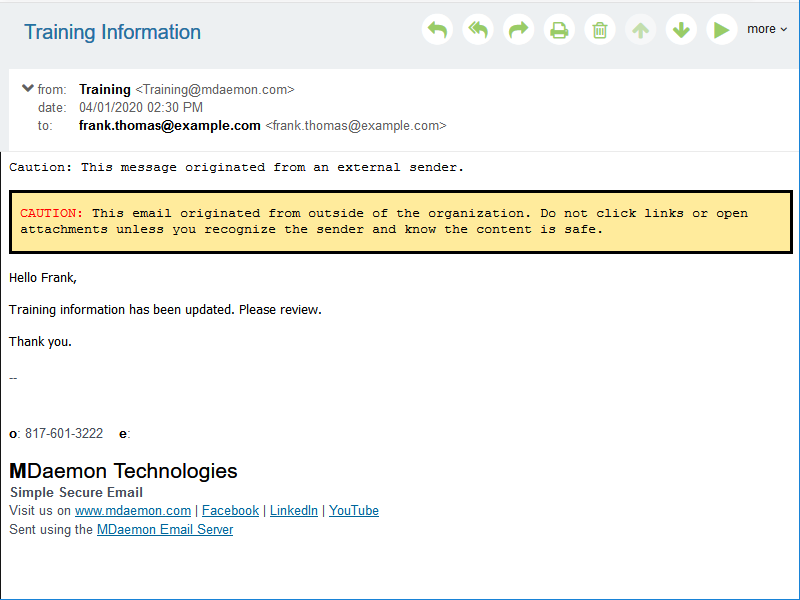
6. Flag emails from external sources with a warning message
Many users who fall for phishing scams are fooled by email spoofing or lookalike domains. To help users identify emails from external sources, MDaemon can display a security warning in the email message to alert users to take extra caution when replying to the email.
7. Implement email filters against known phishing attempt indicators; block suspicious IP addresses
Many phishing emails come from spoofed email addresses, compromised email servers, or clients that have been infected with malware and hijacked as part of a spambot. They may also contain certain commonly-used words or phrases. You can implement filters on your secure email gateway to block these common sources of junk email. You can also block suspicious IP addresses at your firewall.
When in doubt, play it safe!
The bottom line is that we all need to take extra care to avoid getting hooked by email phishing scams, especially during stressful times like these when so many people are seeking solutions. Regularly remind your employees that a few extra seconds of caution could save your entire healthcare organization thousands, or more likely millions, of dollars.


