It’s OK, we understand. You thought you and your employees would all be safely back in the office by now. However, we’re all still adjusting to this new normal of exponentially more remote working – and exponentially more cyberattacks. Every day, hackers seek to exploit not only fear and insecurity caused by the pandemic, but the security loopholes created as more employees access their email and other work systems from remote devices. According to one report, streaming phishing sites saw an 85-percent increase from January to March, with more than 209 malicious websites being created every day. A record 25,000 confirmed phishing pages were created on March 19 alone!
How exactly does the remote-work trend leave your company more susceptible to cyber attacks? The answer, in its shortest form, is people – but it’s true that legacy technological systems may not be helping. Here’s what we mean.
Work Machines, Personal Use
In May, the digital marketing firm Bay Leaf Digital surveyed nearly 800 respondents from more than 30 disciplines who were working from home. The survey found that 65 percent were using company devices from home. The security problem arises because not only are more people working from home, but they’re also using their work machines to access personal sites and apps. Moreover, it’s not unheard of for employees to allow their spouses or kids to use their work machines for other home use such as accessing online schoolwork.
It isn’t hard to imagine how just one sketchy email, just one file download, just one click on the wrong link – by any one of the tens, hundreds, thousands of people who have access to your work devices – could blow open a hole in your carefully constructed security measures. And you likely won’t know until it’s way too late.
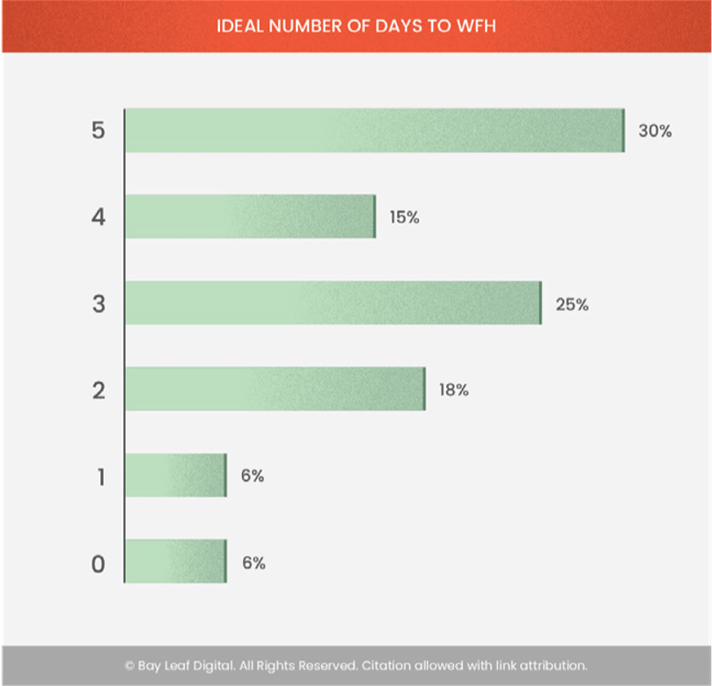
That’s not the only reason you can’t afford to be complacent on this. In the above-referenced survey, senior management seemed to expect that remote work was a temporary solution to be rectified once the pandemic was under control. As a result, 57 percent of senior management was not planning to make any changes as the result of their employees working from home.
However, 70 percent of respondents expressed a desire to work from home three or more days a week, and 30 percent wanted to work from home permanently. Recent estimates predict that, by the end of 2021, 25 to 30 percent of the workforce will still be working at home multiple days a week. Therefore, heightened security for work machines in remote use is likely to be a relevant concern well into the future.
Are your cybersecurity systems – and your employees – ready for that?
Tightening Security for the Long Haul
Your employees may not be, for a couple of reasons:
1. In the Bay Leaf survey, 23 percent of respondents reported unstable remote access to necessary work systems.
2. Beyond technological concerns, most employees need additional training on how to establish strong security measures from home.
Let’s take a closer look at what training your employees are likely to need and what tech defenses can be shored up. We’ll use our Security Gateway for Email product as an example.
Email Security
As long as people continue to fall victim to email-related scams, you will need ongoing employee training on how to spot social engineering, spoofing, business email compromise (BEC) and other phishing-related tactics. A good place to start would be to review these 10 tips to identify a phishing email, and as always, remind them to remain vigilant and be skeptical of any online requests for information.
On the server side, you need real-time anti-spam and antivirus technology that is capable of proactively protecting your email infrastructure automatically and within minutes of an outbreak. Security Gateway scans all inbound and outbound mail using the Cyren and ClamAV antivirus engines. It also includes Cyren Outbreak Protection.
Passwords
In these days of leaked password lists and data breaches, it should surprise no one to hear that simple passwords are easy for hackers to crack. If a spammer guesses an employee’s password, he can then use that account to send out spam. And if that employee uses the same password to access other accounts, such as online banking or utilities, cybercriminals could perpetrate more egregious online crimes, such as identity theft or extortion. Educate your users on password security and consider the use of two-factor authentication on your networks.
To limit the spammer’s ability to abuse a compromised account, Security Gateway includes Account Hijack Detection , where you specify the maximum number of messages that can be sent in a given time frame. Once the limit has been reached, the account is disabled and your administrator is notified. In addition, Security Gateway can be configured to require strong passwords as part of user verification.

Data Leaks
Now let’s talk about the non-people parts of the cybersecurity equation, where data leaks always have to be a concern. Security Gateway includes more than 70 Data Leak Prevention rules to help prevent unauthorized transmission of sensitive information such as personal identification numbers, credit card numbers, and other types of confidential data. These rules can be configured to send messages containing sensitive content to the administrative quarantine for further review, redirect the message to a designated address, or encrypt the message.
Consider the Cloud
Is your hardware-based VPN solving or abetting any problems your employees are having connecting to work systems? Recent consensus seems to be that legacy VPNs often lack the flexibility to adequately connect and secure higher numbers of remote workers with on-premises resources. In other words, if you haven’t already, it might be time to consider a cloud solution to securely and agnostically connect your employees to all your systems, wherever they might be.
At MDaemon Technologies, our cloud-based secure email gateway protects your business with a variety of anti-spam, anti-virus, anti-spyware, anti-phishing, and anti-malware features for inbound and outbound email. It also protects your business with encryption options and data leak prevention, all without the need for administrator intervention.
Better Tech for Busy People
It’s not always easy working from home, and it’s certainly not easy to adjust your systems to secure remote working. Security Gateway was designed to be easy to use while providing the strongest protection against spam, phishing, and data leaks. If you’d like more information on how MDaemon Technologies can help secure your employees’ email, visit SecurityGatewayForEmail.com.