![]()
This week, we learned of a new phishing campaign targeting PayPal users in an attempt to extract as much personal data as possible.
The campaign is spread via an email claiming to be from PayPal’s notification center warning users that their account was accessed from another browser or device. The recipient is then prompted to click on a button which opens an online form owned by the attacker.
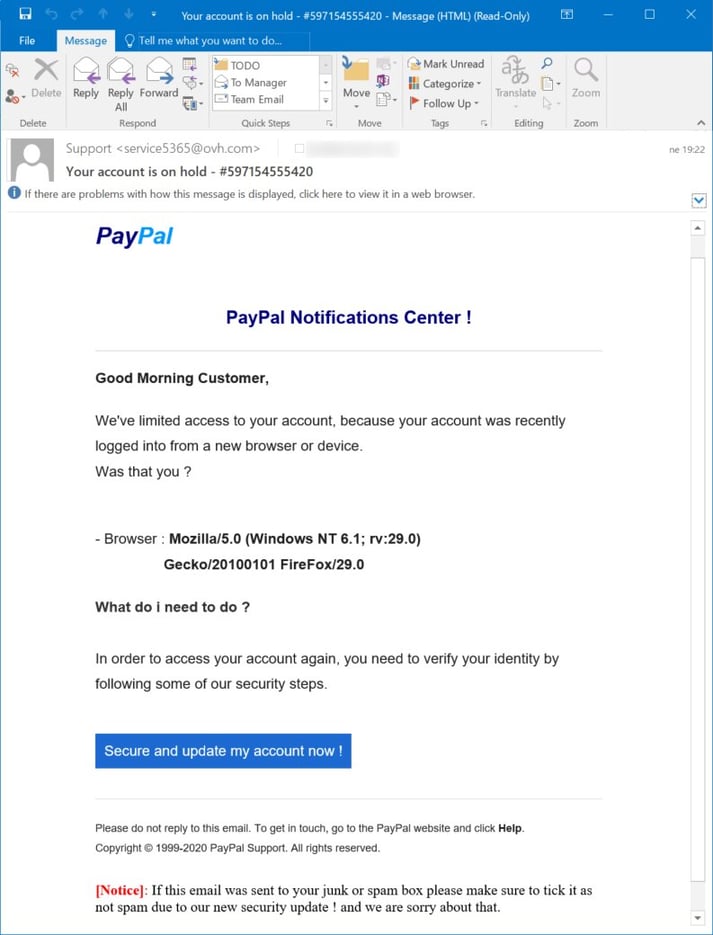 PayPal phishing email (Source: SANS ISC)
PayPal phishing email (Source: SANS ISC)
If you’ve been following some of my previous posts, you may recall that I’ve discussed avoiding phishing email scams fairly frequently, but as long as people continue to fall victim to these and other email related scams, there will be a need for ongoing education on how to spot social engineering, spoofing, and other phishing-related tactics.
Consider this week’s PayPal phishing example. Cybercriminals often take advantage of the fact that many email clients (especially mobile devices) will only show the display name or “friendly from” header, and not the full email address. In the above example, “Support” was used as the display name, but the message was actually sent from an address under ovh.com.
Helpful Tip: To help users identify email spoofing, MDaemon Webmail displays the full email address in the message header.
If a user clicks on the link in the email, they are taken to a landing page operated by the attackers, and then presented with a fake login form where they are prompted to enter their email address and password.
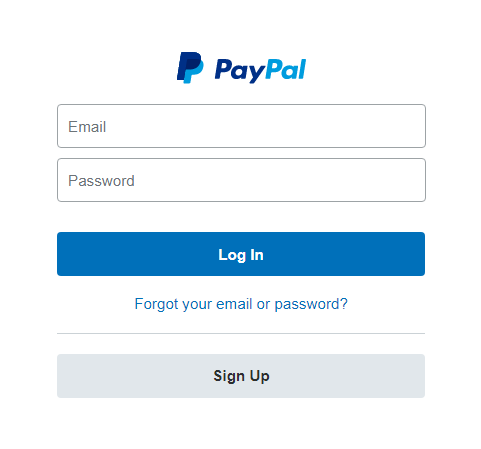
PayPal Login Form on Phishing Site
From there, the user is asked for their full street address, and then they are taken to a form requesting credit card details.
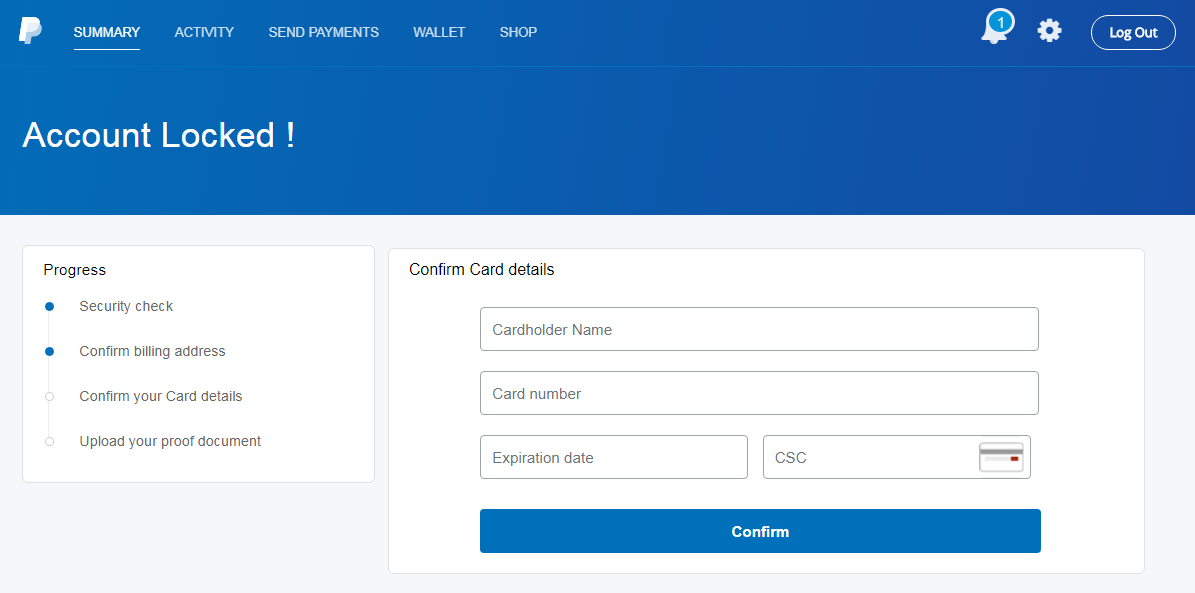 Lookalike PayPal form requesting credit card information
Lookalike PayPal form requesting credit card information
At this point, most users would start getting suspicious, but those who proceed are presented with a form requesting their date of birth, Social Security number, and even their ATM or debit card PIN.
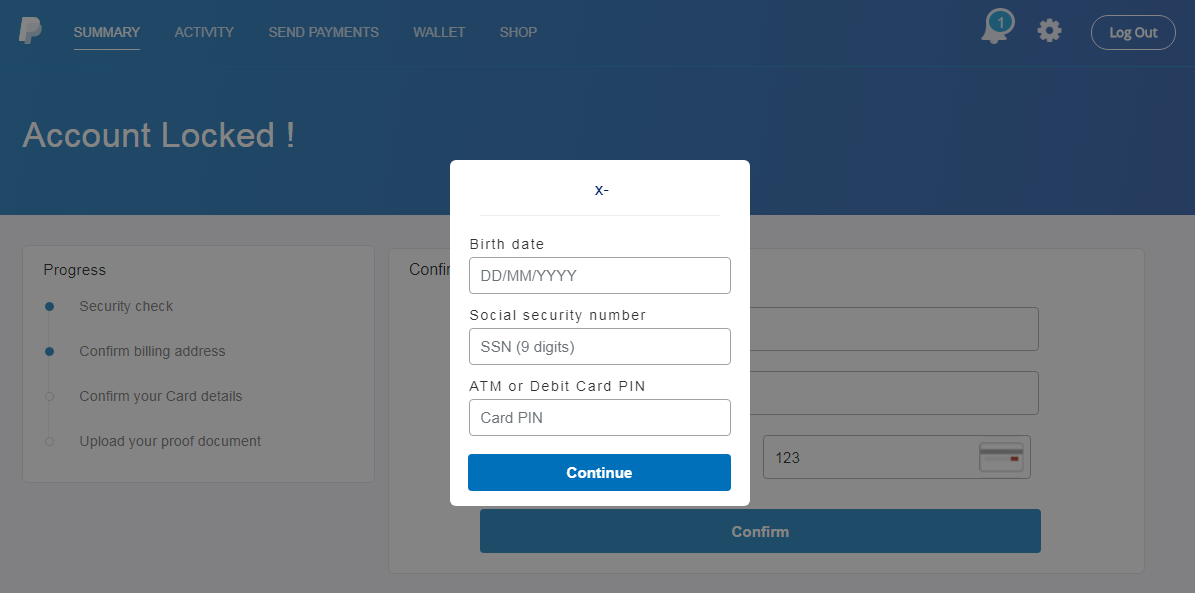 PayPal Account Locked Spoofed Form
PayPal Account Locked Spoofed Form
Users who go a step further are then requested to upload a photo of a valid ID or credit card.
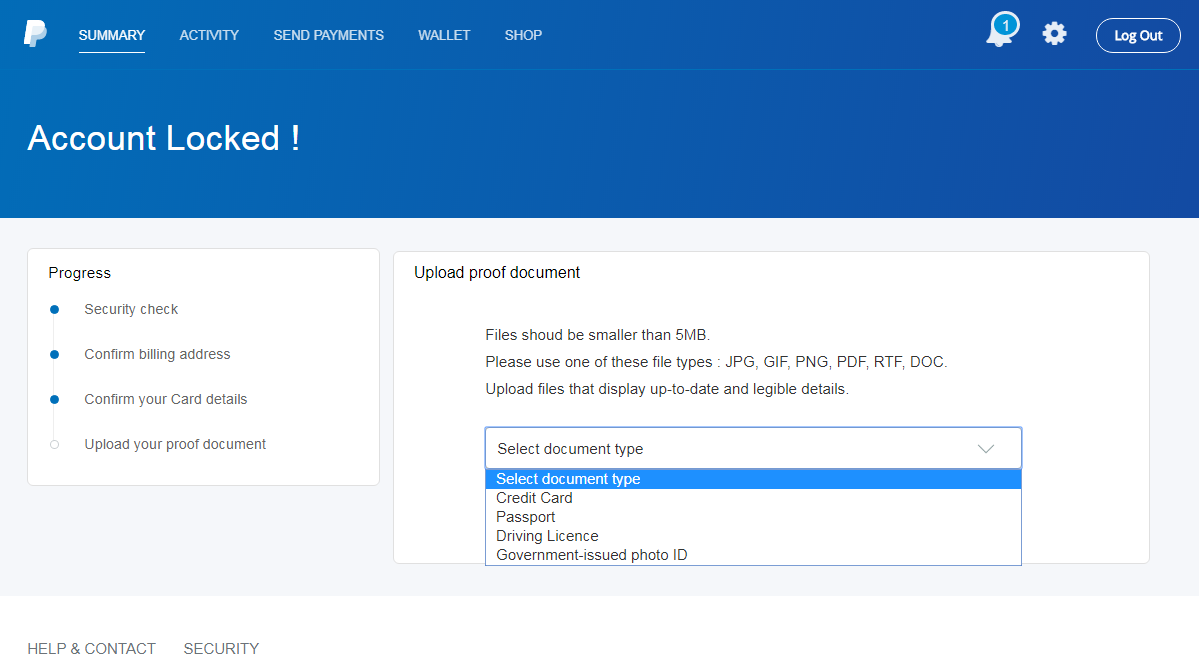 PayPal Phishing Image Upload
PayPal Phishing Image Upload
By this point, most people would recognize this as a phishing scam, but inevitably, enough users will fall for these and other scams to keep cybercriminals in business for the foreseeable future.
Most reputable banking and government institutions have strict policies regarding their handling of confidential information. You’ll find more information on avoiding common email scams on PayPal’s website.
Phishing scams continue to evolve, with enough victims to keep cybercriminals in business for the foreseeable future. That’s why it’s important for businesses of all sizes to provide their employees with ongoing training on how to recognize and avoid email scams. A good place to start would be to review these 10 tips to identify a phishing email, and as always, remain vigilant and be skeptical of any online requests for information.


