Online scams are nothing new. But as email has evolved and improved, so have scammers and the messages they send. Nefarious emails, attachments and links now appear sophisticated and look legitimate, sometimes tricking even the most meticulous user.
Billions Lost to Business Email Compromise
Over the past five years, organizations all over the world have lost over $52 billion to a very specific type of email scam – Business Email Compromise, or BEC.
BEC scams have been around for years, and while many of the same phishing and social engineering tactics continue to be used, these attacks are evolving in complexity and sophistication, especially as AI tools like ChatGPT make it much easier to craft well-written, convincing phishing emails.
BEC Stories in the News
- The Houston office of the FBI and Dutch authorities seized 39 domains used to sell phishing kits and email-extractor tools that were used in BEC schemes.
- Over US $5.3 million forfeited in a Boston case involving funds laundered through intermediary bank accounts and crypto exchanges in Hong Kong, Singapore, Nigeria.
- In Australia, Noosa Council was hit by a BEC scam exploiting AI/social engineering for AU $2.3 million; this shows smaller organizations remain vulnerable.
- A Florida-based international scheme, where a man was extradited from the Dominican Republic in a case of US $60 million+ fraud targeting sports teams, healthcare companies, nonprofits via BEC-style methods.
Why do BEC Scams Work so Well?
BEC emails are advanced phishing scams, and they’re on the rise. But what makes a BEC attack so dangerous, and so effective?
BEC Scams are Highly Targeted
Scammers aren’t blasting thousands of the same email. They’ve done the research, monitoring the company’s website and social pages. They find the appropriate target, and groom them by sending multiple conversational emails, establishing trust.
They Contain No Malware
Unlike the old style of phishing, where users are told to click on a link, BEC emails have no spammy links. This means they can sometimes evade spam filters, and the end user doesn’t see any red flags.
They Exploit Human Nature
BEC emails imitate an actual person, complete with real-looking email addresses, formatting, company names, and titles. The victim has unknowingly been emailing back and forth with the scammer and trusts that they are who they claim to be. So when asked to send bank information, for example, the victim assumes the request is authentic and complies.
They are Often Under-reported
Victims often don’t realize they made a mistake until much later. And even upon realization, many companies don’t report the incident for fear of damaging their reputation with their customers. Not reporting such incidents allows perpetrators to simply move on to their next victim.
Learn How to Stay Protected Against these Email Scams
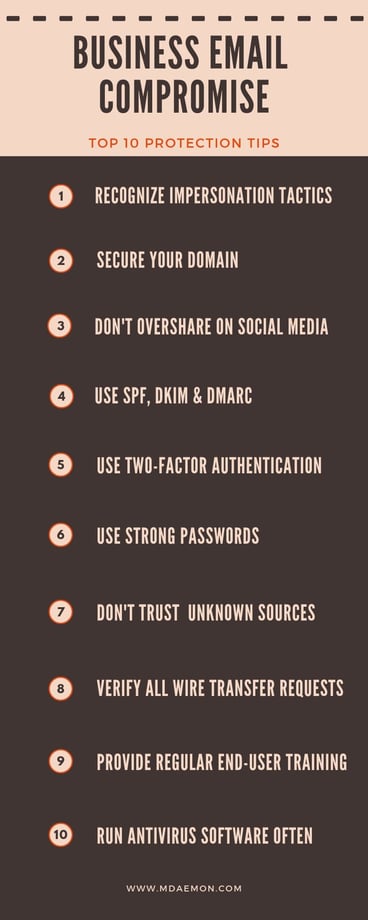
Preventing losses to Business Email Compromise is the responsibility of both the end user and the IT administrator. To stay protected, follow these tips:
End Users:
- Double-check the sender email address & recognize spoofing and other impersonation tactics. MDaemon Webmail displays the full email header to help users identify spoofed emails.
 MDaemon Webmail: Full Email Header Display
MDaemon Webmail: Full Email Header Display - Don’t overshare on social media
- Don’t open email from unknown sources
- Verify all wire transfer requests via phone or face-to-face
- Know customers’ & vendors’ business practices
- Run antivirus software often
- Use two-factor authentication
- Forward, don’t reply. Ensures you manually enter the appropriate email address.
Administrators:
- Enable reverse lookups to verify the legitimacy of the sender
- Use the antivirus features in MDaemon and SecurityGateway to scan all inbound and outbound email traffic
- Require users to use SMTP Authentication
- Use SPF, DKIM & DMARC to secure your domain against spoofing
- Require two-factor authentication
- Require strong passwords
- Provide regular end-user training
- Run antivirus software often and make sure virus signatures are up-to-date
While traditional security measures such as network defenses and email gateways can be effective at blocking most varieties of spam, the bottom line is that the most critical part of stopping BEC attacks is user awareness and education.


