Has this happened to you? Let’s say you’re the MDaemon administrator for your company, and you’ve noticed that somewhere, somehow, spam messages are being sent from within your network. Perhaps one of your PCs has been compromised. What do you do? Here are some tips to help you track the issue down.
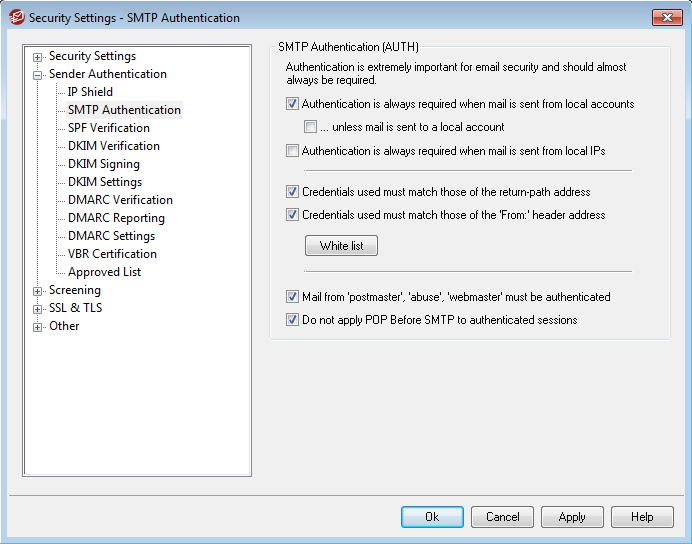
First, make sure you have the option “Authentication is always required when mail is from local accounts” enabled (Security | Security Settings | SMTP Authentication). Also enable “Credentials used must match those of the return-path address” and "Credentials used must match those of the From header address." Then, make sure “…unless message is sent to a local account” is unchecked to prevent intra-domain spam (between local domain users).
Next, find out if the spam messages are coming in from an authenticated session. To do this, locate one of the spam messages & open it up in Notepad to view its headers (or you can open it in Queue & Statistics Manager). Does the message have an X-Authenticated-Sender header? It will look something like this:
X-Authenticated-Sender: SpammerUser@example.com
If this header is present, then that is the user who authenticated to send the message. The first thing you should do in this case is to change the account’s password via the Accounts menu in MDaemon. Even if the spamming is going through the user’s mail client, until you give the user the new password and they update their mail client the authentication credentials will be rejected and the spamming will be temporarily stopped.
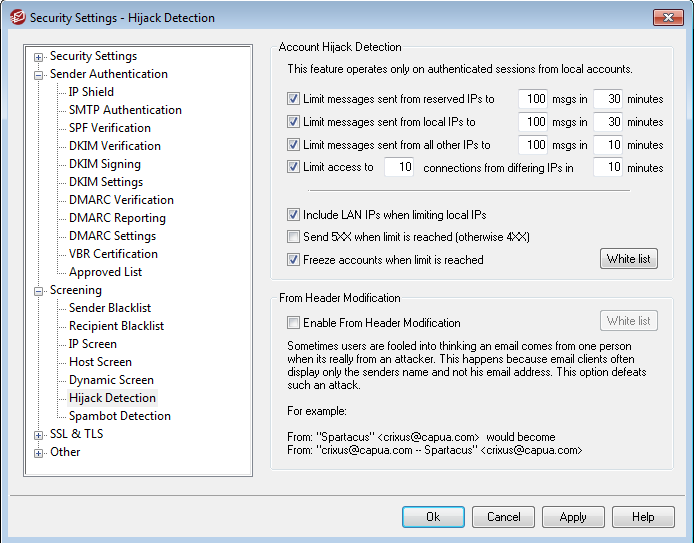
In newer versions of MDaemon, we've added Account Hijack Detection, which will automatically disable an account if it sends a specified number of outbound messages via an authenticated session in a given period of time. We recommend enabling this feature. In MDaemon, it's located under Security | Security Settings | Screening | Hijack Detection.
The next step is to look at the Received headers. Find the one where the message was received by your server. Here is an example of what this header would look like:
Received from computer1 (computer1@example.com (192.198.1.121) by example.com (MDaemon PRO v17) with ESMTP id md50000000001.msg for <UserWhoWasSpammed@example.com >, Fri, 13 Sep 2016 21:00:00 -0800
Find the connecting IP (192.198.1.121) in the above example. This is the machine that is sending out spam. Locate that machine to deal directly with the spambot on that machine.
If the message wasn't authenticated or wasn't sent from your local network, locate the Message-ID header and copy that value.
Message-ID: <123.xyx.someone@example.net>
Then open the MDaemon SMTP-IN log that covers the time when that message was received by MDaemon (based on the timestamp in the received header) and search for that Message-ID in the log (in the 250 response line when the message is accepted):
Thu 2016-09-12 20:00:00: --> 250 Ok, message saved <Message-ID: <123.xyx.someone@example.net>>
Look at the rest of transaction and see why the message was accepted/not rejected - spam score, DNSBLs, etc.
Also, if your external domain is listed in the Trusted Hosts list (Security | Security Settings | Trusted Hosts), try removing it from this list.
Check back often for more tips & tricks!