This week, we continue our series on Business Email Compromise. Click here to read Part 1, which includes an overview and various statistics on this growing threat.

It takes time and effort to launch a successful Business Email Compromise (BEC) attack. In a typical attack, several email messages are exchanged in an attempt to convince the target to authorize large payments to the attacker’s bank account. From start to finish, the steps involved in a BEC attack consist of identifying a target, grooming, exchanging information, and finally, transfer of funds.
Let’s go over these four steps in detail.
Step 1 – Identify the Target Victim

The first step in a BEC attack may be the most time-consuming. During this step, a criminal organization researches the victim to develop an accurate profile of the company. Through publicly available information found on LinkedIn, Facebook, Google, and other sites, attackers look for the names and positions of company executives or employees who have access to employee records or financial data. They scour social media, online articles, and anything else that will provide specific details about the company and its employees. Scammers who are able to infiltrate a company’s network with malware may spend weeks or months monitoring information on the company’s vendors, billing and payment systems, and even employee vacation schedules. They have also been known to monitor the executive’s writing style in order to craft a convincing email using a spoofed email address or lookalike domain claiming to come from the CEO.
Step 2 – Grooming

Armed with the information obtained in Step 1, the scammer moves on to Step 2- the Grooming phase. During this step, the scammer uses spear-phishing, phone calls or other social engineering tactics to target employees with access to company finances. The grooming process often takes several days of back and forth communication in order to build up trust. During this phase, the scammer may impersonate the CEO or another company executive and use his or her authority to pressure the employee to act quickly.
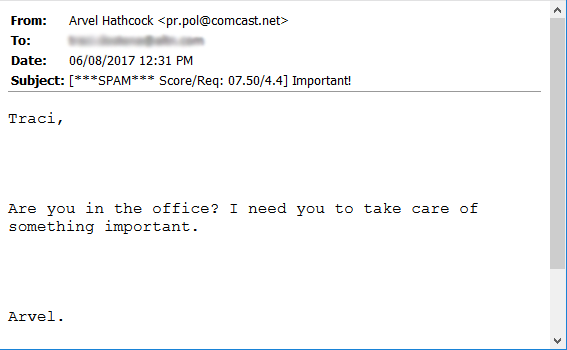
Here is an example sent to one of our Finance executives in which the sender used display name spoofing to spoof the name of our company founder. Cybercriminals will often use a free email address (notice the comcast.net domain), which can be easy to miss if you're using a mobile device or some other client that doesn't display the full email header. (Note: To help the recipient identify potential phishing or spoofing, MDaemon Webmail displays the full email address taken from the message headers.)
Step 3 – Exchange of Information

During step 3, the victim is convinced that he is conducting a legitimate business transaction, and is then provided with wire transfer instructions.
Once the victim is convinced that he or she is conducting a legitimate business transaction, the scammer sends the victim instructions for transferring the funds into a bank account belonging to the cybercriminal organization.
Step 4 – Payment

And finally, funds are transferred and deposited into a bank account controlled by the criminal organization.
What to Do if You Are a Victim
If you’ve suffered losses due to Business Email Compromise schemes, it is important to act quickly.
- Contact your financial institution immediately.
- Request your financial institution contact the institution that received the fraudulent funds.
- Contact your local FBI office and report the incident.
- File a complaint with the FBI’s Internet Crime Complaint Center (IC3).
You can find more detailed instructions in the FBI's Public Service Announcement.
Want to learn more about how to protect yourself from Business Email Compromise scams? In Part 3, we’ll go over a few best practices, so check back soon!


