Discover the latest technique cybercriminals use to deceive victims and gain unauthorized access to sensitive information.
Understanding the concept of pretexting
Have you ever felt so comfortable that you simply go with the flow and make decisions without much thought? If so, you're likely an easy victim for pretexting scammers.
Pretexting is a deceptive technique used by cybercriminals to trick individuals into divulging sensitive information. It involves creating a false pretext or scenario to gain the trust of the victim. The attacker often poses as a trustworthy individual or organization, such as a bank representative or a colleague, to manipulate the victim into providing personal or confidential data.
By understanding the concept of pretexting, individuals can become more aware of the tactics used by cybercriminals and take necessary precautions to protect themselves.
Pretexting vs traditional phishing
While traditional phishing involves sending mass emails to a large number of people in the hopes of tricking a few into revealing their sensitive information, pretexting takes a more targeted approach. Pretexting attackers carefully research their victims, gathering information from various sources like social media or public records, to create a convincing scenario that is tailored to the victim's interests or needs.
Unlike traditional phishing, which relies on the victim clicking on a malicious link or downloading a file, pretexting often involves direct communication with the victim, either through phone calls, emails, or in-person interactions. This personal touch makes pretexting attacks more sophisticated and difficult to detect.
How pretexting works
Pretexting attacks typically follow a specific process. First, the attacker selects a target and gathers information about them. This information can include personal details, work history, or even the names of friends or family members. With this information in hand, the attacker then creates a plausible scenario that will convince the victim to divulge sensitive information.
For example, an attacker may pose as a bank representative and contact the victim, claiming that there has been suspicious activity on their account. They will then ask the victim to verify their account details or provide additional information to resolve the issue. The victim, believing they are speaking to a legitimate bank representative, may unknowingly provide the attacker with their login credentials or other sensitive data.
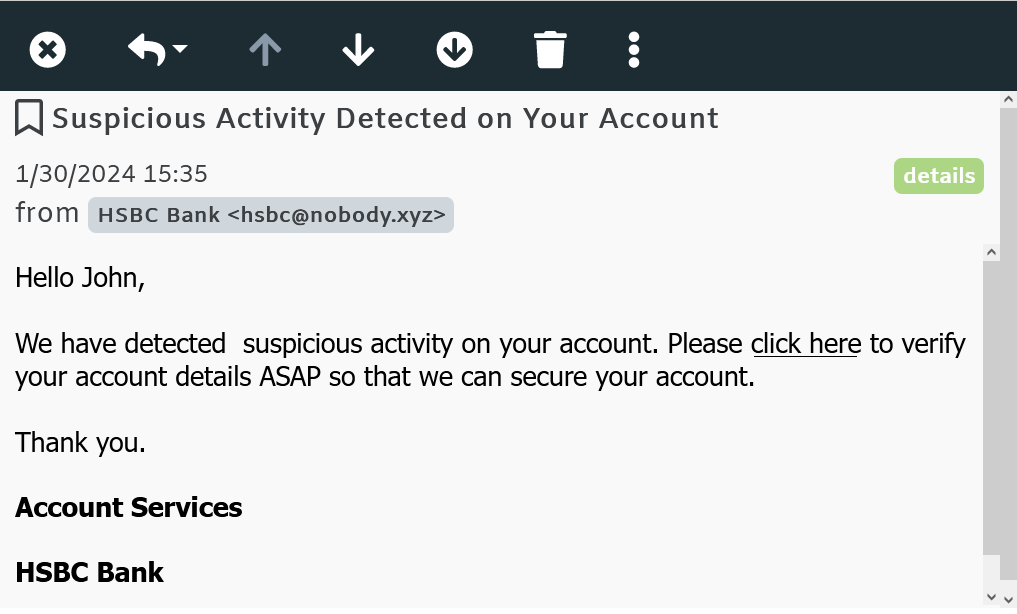
Pretexting attacks can also involve impersonating a trusted individual or organization to manipulate the victim into performing certain actions. This can include requesting wire transfers, changing passwords, or even installing malware on their device.
Common scenarios of pretexting attacks
There are several common scenarios in which pretexting attacks occur. One example is when an attacker poses as an IT support technician and contacts an employee, claiming there is an issue with their computer or network. The attacker may then request the employee's login credentials or ask them to download and install malicious software under the guise of fixing the problem.
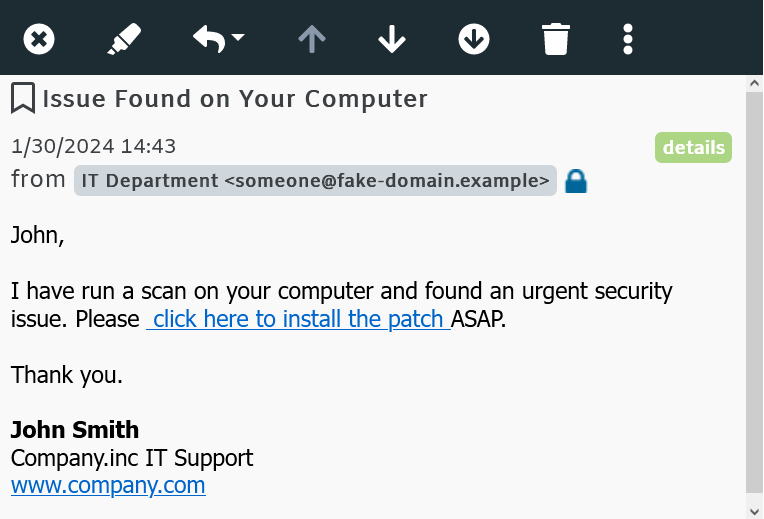
Another common scenario is when an attacker impersonates a company executive or a high-ranking official and contacts an employee, requesting sensitive company information or access to secure systems. The attacker may use various tactics, such as urgency or authority, to manipulate the employee into complying with their requests.
As you may have guessed by now, pretexting uses many similar techniques to those found in Business Email Compromise (BEC) or CEO fraud phishing attacks, which I've discussed in this article.
It is important to be cautious and verify the legitimacy of any requests for sensitive information, especially when they come from unexpected or unfamiliar sources.
Protecting yourself against pretexting
Protecting yourself against pretexting attacks requires a combination of awareness and caution. Here are some measures you can take to minimize the risk:
- Be cautious of unsolicited requests for personal or sensitive information, especially if they come from unfamiliar sources.
- Verify the identity of individuals or organizations before providing any information or performing any actions.
- Limit the amount of personal information you share on social media platforms or public records.
- Keep your computer and mobile devices updated with the latest security patches and antivirus software.
- You can configure MDaemon Email Server to check for updates automatically via Setup | Preferences | Updates.
- You can configure SecurityGateway to check for updates automatically via Setup / Users | Software Updates
By being vigilant and proactive, you can significantly reduce the chances of falling victim to pretexting attacks.
Take advantage of the latest security features found in MDaemon and SecurityGateway. Download your free 30 day trial!


