It's just a fact of life: If there's email, there will always be spam. If you’re involved with email security for a healthcare organization, 2020 is absolutely the year you can’t afford not to take this seriously. The healthcare sector has become a major target for cyberattacks during the COVID-19 pandemic, and these attacks are successful so often that Becker’s Hospital Review publishes a monthly update on healthcare provider malware, ransomware and phishing incidents. The most recent list includes:
- An employee of Houston-based Legacy Community Health Services responded to a phishing email that allowed unauthorized access to thousands of patients' information.
- Magellan Health and eight of its entities reported email hacking incidents affecting 364,892 individuals' health information due to a ransomware attack. The hacker got in through a phishing email impersonating a client and accessed a corporate server that stored personal information including names, Social Security numbers, health insurance account information, tax details and addresses of clients.
- The Central California Alliance for Health, a nonprofit Medicaid health plan, notified 35,883 members of an employee email hacking incident that exposed their information.
Clearly, no one wants to be the healthcare organization that has to send out that notification to its patients. But your organization’s first line of defense doesn’t have to rely on humans; how much spam your employees have to deal with depends on how good your spam filtering solution is. Here at MDaemon Technologies, we built MDaemon and Security Gateway for Email to filter out spam, malware, phishing attempts, and all of the other junk that often floods inboxes of users whose email server or hosted email security service’s filters aren’t as effective.
"If we have a good spam filter, do I REALLY need to know how to recognize phishing scams?"
If an email security company or hosted provider tells you their spam filter will catch 100% of spam, they're not being completely honest. Most companies specify their products will catch 99% or 99.5% in their SLA (Service Level Agreement), with a false-positive rate of %.0001 or less. That's reasonable and to be expected, especially considering the statistics.
According to public data, spam made up more than 29% of global email traffic in 2019. Considering that an estimated 306 billion email messages are being sent per day worldwide in 2020, that's almost 89 million spam messages sent every day. In addition, spam is becoming more dangerous, with cryptojacking overtaking ransomware as the attack vector of choice for cybercriminals, and malware-as-a service turning cybercrime into a commodity for the masses.
So no matter how good an email security product is, there is always that chance that new and emerging (and sometimes tried-and true) social engineering techniques will succeed in tricking one of your employees into parting ways with the keys to your company's financial or patient information.
That brings me to the point of today's post: It bears repeating that healthcare organizations of all sizes should consider ongoing training with their employees on how to recognize phishing attempts.
In today's example, the scammer is using a classic BEC (Business Email Compromise) attack to try to get the recipient to open a malicious ISO file.
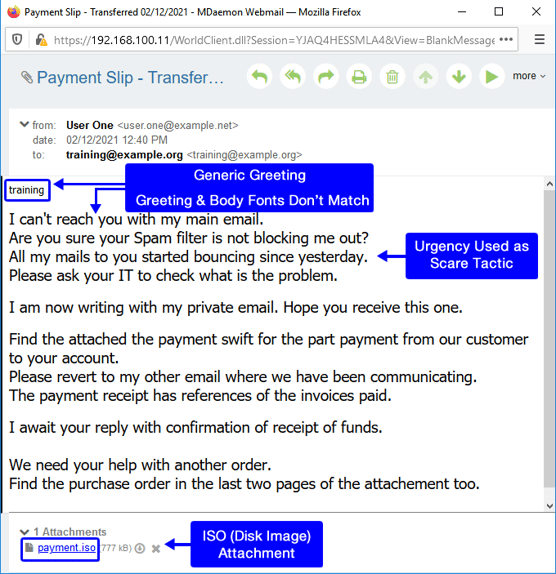
Phishing email using common Business Email Compromise tactics
Phishing email using common Business Email Compromise tactics
Because the threat of phishing and Business Email Compromise will continue well into the future, make sure to check out this related post for the healthcare industry.
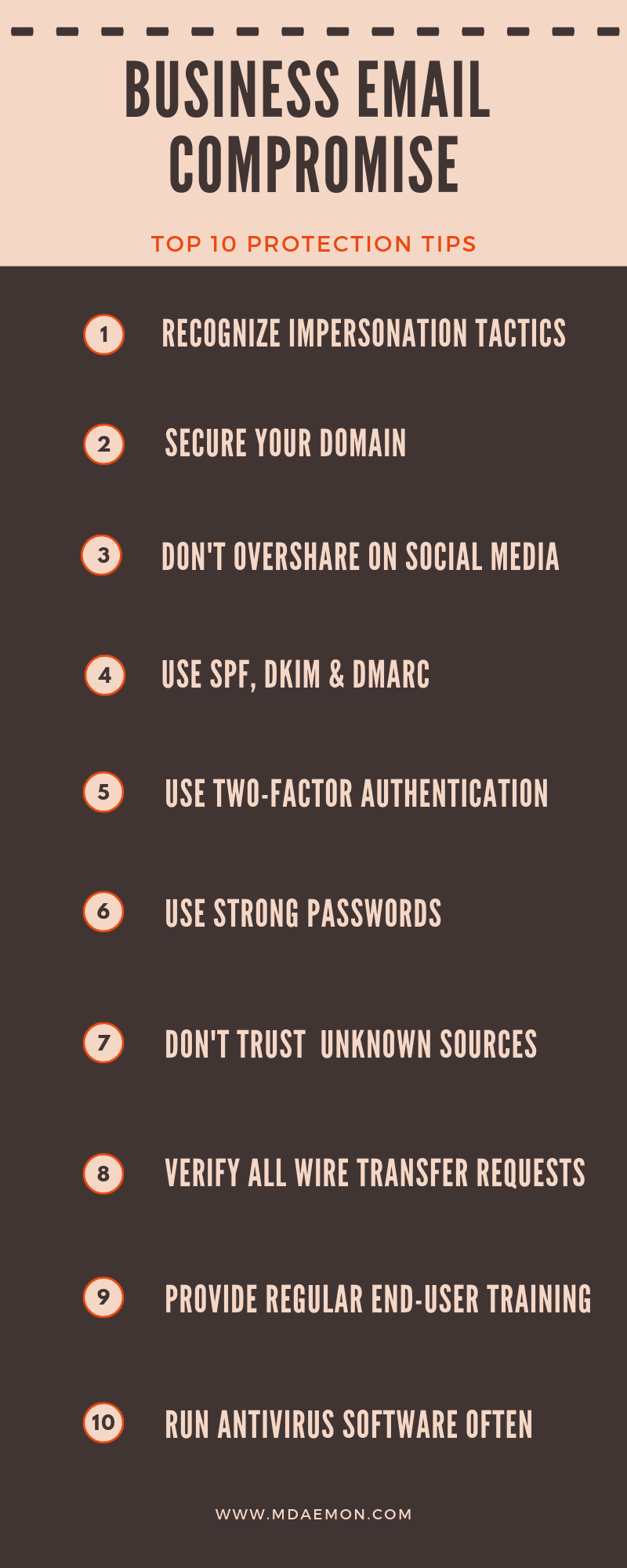
Meanwhile, I would recommend sharing with all employees, healthcare providers and even third-party vendors these 10 best practices for avoiding common email scams.