Discover the best practices for securing your email communications with DMARC and its importance in preventing email fraud and phishing attacks.
Understanding the Basics of DMARC
DMARC, which stands for Domain-based Message Authentication, Reporting, and Conformance, is an email authentication protocol that helps protect your domain from email spoofing, phishing, and other fraudulent activities. It allows email senders to specify which email servers are authorized to send emails on their behalf, and it enables email receivers to verify the authenticity of incoming emails.
By implementing DMARC, you can gain greater control over your domain's email delivery and enhance your email security. DMARC works by combining two existing email authentication protocols: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). SPF verifies that an email comes from an authorized IP address, while DKIM verifies that the email content has not been tampered with.
This diagram provides an overview of how DMARC works.
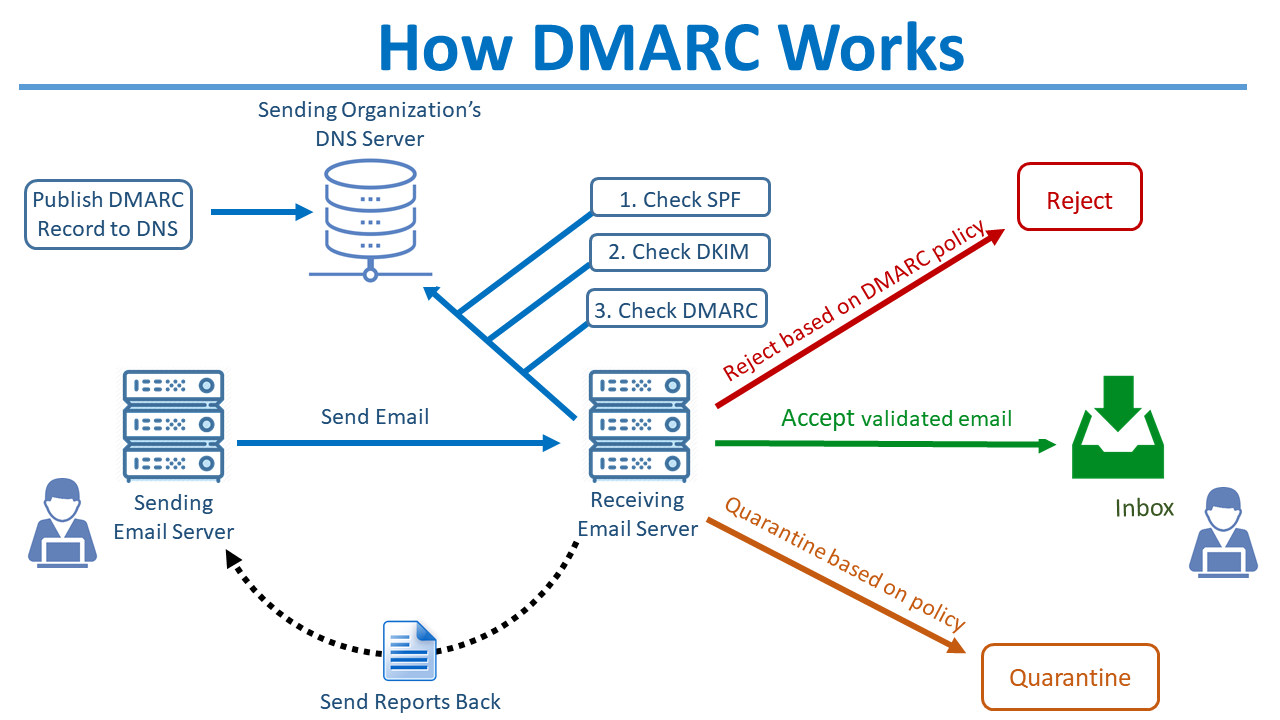
For more information on setting up SPF & DKIM in MDaemon® Email Server, please see the following knowledge base articles:
- How to Enable SPF Verification & Create a Simple SPF Record
- How do I enable DKIM signing and configure primary and additional domain records?
With DMARC, you can specify how email receivers should handle emails that fail SPF and DKIM checks. You can choose to have the emails rejected, quarantined, or simply monitored. Additionally, DMARC provides valuable reporting data that allows you to monitor and analyze the email traffic originating from your domain.
Watch our video to learn more on how SPF, DKIM & DMARC work together to help protect businesses against email spoofing
Why Use DMARC for Email?
Using DMARC for email is crucial for maintaining the integrity of your email communications and protecting your brand reputation. Here are a few reasons why you should consider implementing DMARC:
1. Prevent Email Spoofing: DMARC prevents unauthorized senders from sending emails on behalf of your domain, reducing the risk of email spoofing and impersonation.
2. Reduce Phishing Attacks: Phishing attacks involve fraudulent emails that trick recipients into providing sensitive information. DMARC helps prevent such attacks by verifying the authenticity of incoming emails.
3. Enhance Deliverability: By implementing DMARC, you can improve your email deliverability rates and reduce the chances of your legitimate emails being marked as spam or phishing attempts.
4. Gain Visibility and Control: DMARC provides detailed reporting data that allows you to gain insights into your email traffic and take proactive measures to protect your domain.
Overall, using DMARC for email helps ensure that your emails are genuine, secure, and trusted by your recipients.
Implementing DMARC Best Practices
To implement DMARC effectively, it is important to follow these best practices:
1. Start with Monitoring: Before enforcing DMARC policies, start by monitoring your email traffic and analyzing the DMARC reports. This will give you insights into your current email practices and help identify any issues or unauthorized senders.
2. Implement SPF and DKIM: Ensure that your domain has SPF and DKIM records properly set up. SPF verifies the authorized IP addresses for sending emails, while DKIM signs your outgoing emails to help receiving domains verify their authenticity.
3. Set Up DMARC Policy: Gradually enforce DMARC policies by starting with a monitoring-only policy (p=none). This allows you to gather data on email sources and potential issues without impacting email delivery.
DMARC records use a "p=" tag to indicate the DMARC policy. This tag will be one of the following: p=none, p=quarantine, or p=reject.
Here is an example of a DMARC record showing its policy:
v=DMARC1; p=none; rua=mailto:dmarc@example.com
4. Analyze and Adjust: Regularly review the DMARC reports to identify any anomalies or unauthorized senders. Adjust your DMARC policy accordingly to reject or quarantine suspicious emails.
5. Collaborate with Partners: Work with your email service providers, partners, and vendors to ensure that they also implement DMARC and adhere to best practices. This helps create a secure email ecosystem and protects all parties involved.
By following these best practices, you can effectively implement DMARC and enhance your email security.
Monitoring and Analyzing DMARC Reports
Monitoring and analyzing DMARC reports is an essential part of maintaining email security. DMARC reports provide valuable insights into your email traffic, including information about authorized and unauthorized senders, email authentication failures, and potential phishing attempts.
Here is an example of a DMARC report.
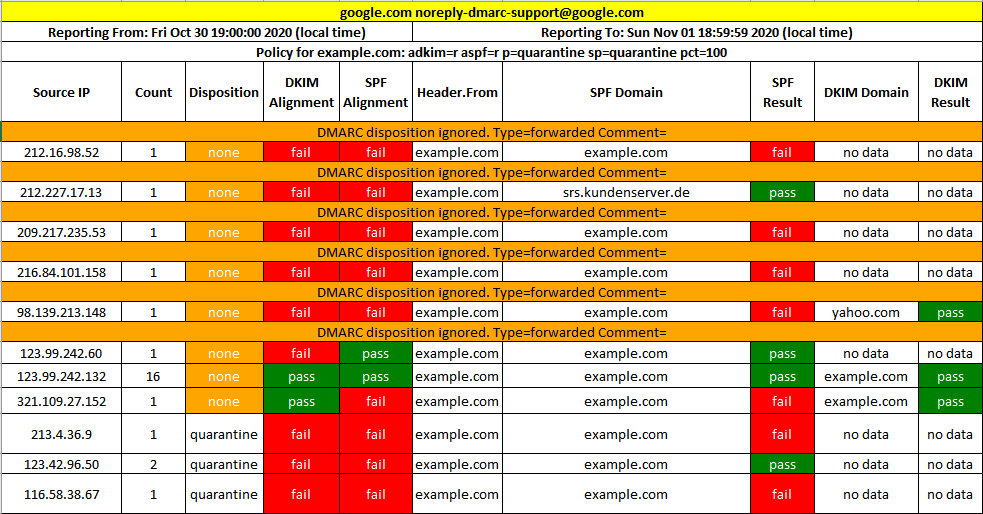
To effectively monitor and analyze DMARC reports, consider the following:
1. Regularly Review Reports: Set up a process to regularly review the DMARC reports to identify any anomalies or suspicious activities. Pay attention to email sources that fail SPF or DKIM checks and investigate them further.
2. Use Reporting Tools: There are various DMARC reporting tools available that can help you analyze the reports and visualize the data. These tools can provide valuable insights and make it easier to identify patterns and potential threats.
3. Take Action on Suspicious Emails: If you identify any suspicious emails or unauthorized senders in the DMARC reports, take appropriate action. This can include quarantining or rejecting the emails and investigating the source of the emails.
4. Adjust DMARC Policy: Based on the insights gained from the DMARC reports, adjust your DMARC policy accordingly. Strengthen your policies to reject or quarantine suspicious emails and update your SPF and DKIM records if necessary.
Staying Ahead of Email Fraud and Phishing Attacks
Email fraud and phishing attacks continue to be major threats in the digital landscape. To stay ahead of these attacks, consider the following measures:
1. Employee Education: Educate your employees about email security best practices, including how to identify phishing emails, avoid clicking on suspicious links, and report any suspicious activities.
2. Multi-Factor Authentication: Implement multi-factor authentication (MFA) for your email accounts to add an extra layer of security. This can help prevent unauthorized access even if the account credentials are compromised.
3. Use App Passwords: App passwords allow users to have a separate password for each connection to their inboxes. This means they can have one strong password for webmail, another for their Outlook client, and yet another one for their ActiveSync connection on their mobile device. Click here to learn more about using App Passwords in MDaemon Email Server.
4. Regular Security Updates: Keep your email systems and software up to date with the latest security patches. This helps mitigate known vulnerabilities and reduces the risk of successful attacks.
5. Conduct Security Audits: Regularly perform security audits of your email infrastructure and systems. This can help identify any weaknesses or potential entry points for attackers.
6. Stay Informed: Stay updated on the latest email fraud and phishing attack techniques. Keep track of industry news, security advisories, and best practices to ensure you are well-prepared to tackle emerging threats.
By implementing these measures and staying vigilant, you can protect your email communications from fraud and phishing attacks, ensuring the security and trustworthiness of your messages.
Take advantage of the DMARC features in MDaemon. Download your free trial!



