In the past, businesses have often used more relaxed standards for marketing via email. However, GMail has recently begun to enforce stricter authentication requirements for emails sent to Google users. As a result industry leaders have begun using a more targeted, personalized approach to email communication with prospective customers.
So what does this mean for your business?
All domains used for email communication should implement DMARC to authenticate their business communications. This practice was intended primarily for B2C communication but is good practice for B2B as well.
DMARC Deployment Best Practices
We recommend following these best practices when deploying DMARC:
1. Start with Monitoring: Before enforcing DMARC policies, begin by monitoring your email traffic and analyzing the incoming DMARC reports sent from external domains. These reports will give you insights into your current email practices and help you identify any issues or unauthorized sending mail servers.
2. Implement SPF and DKIM: Ensure that your domain has SPF and DKIM records properly configured. SPF verifies that emails are sent from an authorized mail server or gateway, while DKIM signs your outgoing emails to help receiving domains verify their authenticity.
- How to enable SFP Verification in MDaemon and create a simple SPF record
- How to enable DKIM signing in MDaemon and configure DKIM records
3. Set Up Your DMARC Policy: Use rua= and ruf= tags to indicate where aggregate and forensic DMARC reports should be sent. Gradually enforce DMARC policies by starting with a monitoring-only policy (p=none). This allows you to gather data on email sources and potential issues without impacting email delivery.
DMARC records use a "p=" tag to indicate the DMARC policy. For example: p=none, p=quarantine, or p=reject.
Here is an example of a DMARC record showing its policy:
v=DMARC1; p=none; rua=mailto:dmarc@example.com
When first deploying DMARC, it's a good idea to start out with a policy of p=none. This means email messages claiming to come from your domain that don't properly align with DMARC will not be quarantined or rejected. You can use this period to analyze incoming DMARC reports to verify proper alignment with SPF and DKIM.
4. Analyze and Adjust: Regularly review the DMARC reports to identify any anomalies or unauthorized senders. If you notice legitimate sending mail servers or gateways that are not reflected in your SPF record, then update your SPF record to include all sending servers and gateways. Use these reports to eliminate any issues with DKIM signing, for example, legitimate messages from your domain that are not yet properly signed by DKIM.
Once you've verified proper SPF and DKIM implementation, you can set your DMARC policy to p=quarantine while you continue to monitor incoming reports for any remaining issues with DKIM and SPF. A good starting strategy would be to use the pct= tag in your DMARC record. The pct= tag allows you to specify a given percentage of emails that should be handled based on your DMARC policy.
For example, if you have a policy of p=quarantine, you can start out with a pct= tag of pct=20. This indicates that 20% of all messages that do not properly align with SPF and DKIM should be quarantined, while the remaining 80% should be delivered.
Take some time to continue monitoring incoming reports, and then gradually increase the pct= tag (example: pct=50, pct=80).
After you've had some time to monitor your DMARC reports with a policy of p=quarantine, and after any remaining SPF and DKIM issues have been sorted, out, you can then change your DMARC policy to p=reject.
Again, after changing your DMARC policy to p=-reject, consider using the pct=tag, ramping up from a low number gradually until you've had more time to monitor incoming DMARC reports. Once you're comfortable that SPF and DKIM are properly implemented for all legitimate sending servers sending on behalf of your domain, you can remove the pct= tag from your DMARC record.
5. Collaborate with Partners: Work with your email service providers, partners, and vendors to ensure that they also implement DMARC and adhere to best practices. This helps create a secure email ecosystem and protects all parties involved.
Monitoring and Analyzing DMARC Reports
Monitoring and analyzing DMARC reports is an essential part of maintaining email security. DMARC reports provide valuable insights into your email traffic, including information about authorized and unauthorized senders, email authentication failures, and potential phishing attempts.
Here is an example of a DMARC report.
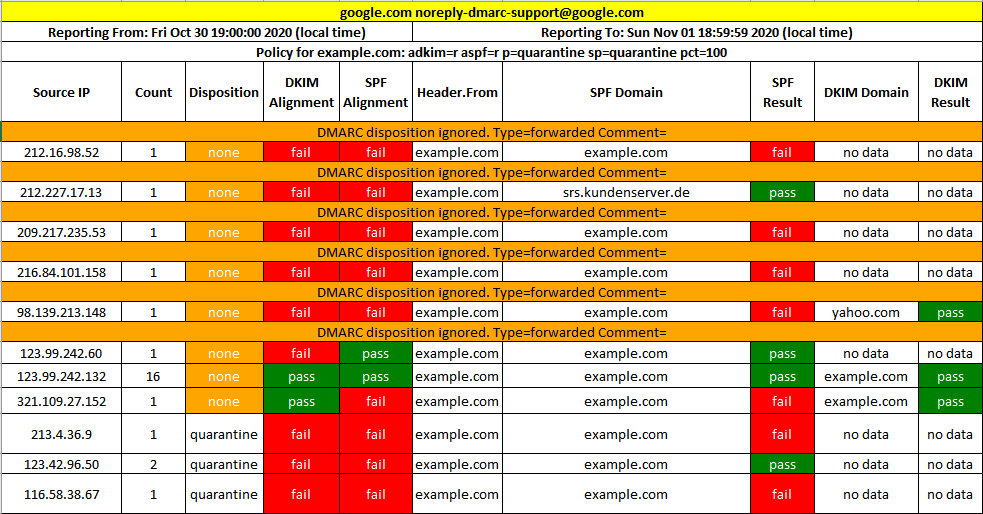
To effectively monitor and analyze DMARC reports, consider the following:
1. Regularly Review Reports: Set up a process to regularly review your DMARC reports to identify any anomalies or suspicious activities. Take note of any email sources that fail SPF or DKIM checks and investigate them further.
2. Use Available Reporting Tools: There are various DMARC reporting tools available that can help you analyze the reports and visualize the data. These tools can provide valuable insights and make it easier to identify patterns and potential threats.
3. Take Action on Suspicious Emails: If you identify any suspicious emails or unauthorized senders in the DMARC reports, take appropriate action. This can include quarantining or rejecting the emails and investigating the source of the emails.
4. Update DMARC Policy: Based on the insights gained from the DMARC reports, adjust your DMARC policy accordingly. Strengthen your policies to reject or quarantine suspicious emails and update your SPF and DKIM records if necessary.
What do Google's new email policies mean for your business?
Businesses that use outbound email as part of their marketing efforts will be held to stricter standards of email authentication enforcement. While this may mean fewer prospects will receive your marketing emails, those that do will likely have a better chance of converting into viable sales leads.


