
A brief glance through my spam folder in MDaemon Webmail recently reminded me of the need for on-going education on the topic of phishing and Business Email Compromise (BEC) scams. I’d like to be able to tell you that the recent crush of cyberattacks on the healthcare sector, as exacerbated by the COVID-19 pandemic, has run its course – but then I’d be the one scamming. Looking through the latest Health IT Security monthly news archive turns up a long litany of phishing, ransomware, malware, spoofing, password theft and other data leaks, and server vulnerabilities that affect millions of patients and financial donors – and it’s not even the end of the month.
Because healthcare organizations have already lost millions of dollars to these scams and continue to fall victim every day, it bears repeating that, while spam filters and secure email gateways continue to improve, no solution is 100% fool-proof.
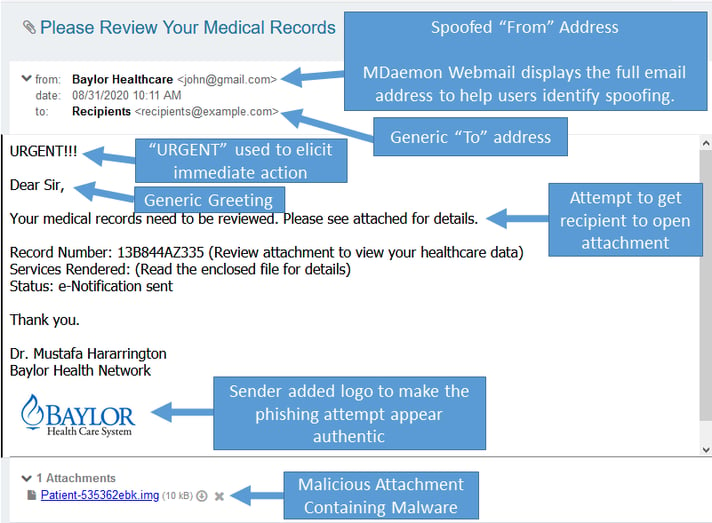
Today's phishing example was scanned by MDaemon, determined to be spam, and placed in my spam folder for review (although MDaemon can also be configured to delete spam instead of placing it in the user's spam folder).
In this example, the scammer has used display name spoofing to make the message appear to be from Baylor Healthcare (recently renamed Baylor Scott & White). Most large healthcare organizations have policies regarding privacy and email communications. You can read Baylor Scott & White’s privacy policy here on their website.
But for most of us who remain unaware of Baylor’s policies, it's important to know what to look for to avoid becoming the next victim of phishing scams.
Using the healthcare example, I've labeled the items to look out for when reviewing a suspicious email.
No healthcare facility is too big or too small to educate its employees about phishing. After all, it only takes one user to open a malicious attachment and unleash malware vicious enough to take down an entire healthcare network. Learn more about how to avoid being the next victim by reviewing these 10 tips to help healthcare employees identify a phishing email.


