While many businesses are moving their email from on-premises to the cloud, many that have already made the switch have discovered that cloud hosted email has its share of drawbacks to go along with the benefits these businesses had originally sought.
Office 365 Vulnerabilities Every Business Should Consider
By Brad Wyro posted in Industry Insight, Two-Factor Authentication, Email Best Practices
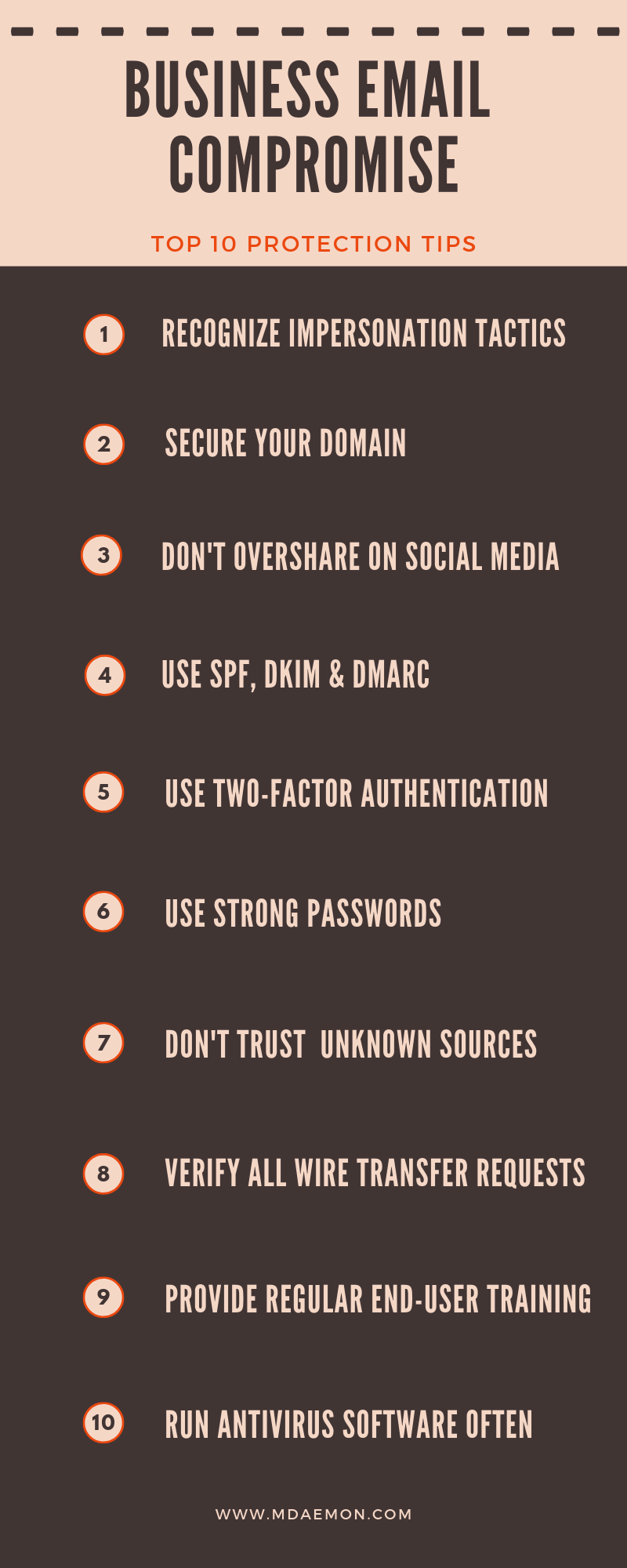
Best Practices to Avoid Business Email Compromise & CEO Fraud Attacks
By Brad Wyro posted in Email Security, Two-Factor Authentication, Email Best Practices
In part one of our three-part series on Business Email Compromise (BEC), I explained what a BEC attack is and provided examples and statistics. As you’ll recall from the examples discussed, businesses have suffered staggering losses to these attacks, and while users are becoming more aware of them, their own human nature dictates that these threats will continue. In fact, a recent report by Get Safe Online indicated that over a third (37%) of employees don’t know what to look for to identify common email scams. The report also stated that one in 20 email fraud victims were so ashamed that they hid their mistakes from their colleagues.
18 Email Safety Tips Every User Should Know
By Brad Wyro posted in Email Security, Two-Factor Authentication, Email Best Practices
Follow these 15 email server security tips to avoid being blocklisted
By Brad Wyro posted in Email Security, Two-Factor Authentication, Email Security Trends, Email Best Practices
With the prevalence of spam & phishing attacks circulating the globe in massive amounts, it becomes increasingly important for email administrators to understand the potential causes of their IP address ending up on a blocklist. Spammers employ all kinds of tricks to try to send out as many spam messages as possible without revealing their identities. They do this through various techniques such as social engineering, employing malware, botnets, forging of message headers, and exploiting weaknesses in email systems or network infrastructures. For the spammer, it’s basically a numbers game. It costs next to nothing to send out thousands of spam messages, and if even a small handful of people click on a link or purchase a product advertised in a spam message, the spammer can profit.
If your email infrastructure is not properly secured, then you risk being infected with malware and becoming part of a spam botnet. Even if your server is not infected with malware, if your firewall and mail server security settings are not configured properly, your IP address could wind up on a blocklist.
To protect your mail server from being blocklisted, consider the following recommendations:
SSL & TLS Best Practices
By Brad Wyro posted in Email Security, Email Encryption, Email Security Best Practices, Two-Factor Authentication, Email Security Trends, Email Best Practices
You may have heard the terms SSL and TLS, but do you know what they are and how they’re different?
Here's how to improve slow Microsoft Outlook performance
By Brad Wyro posted in Email Gateway How-To, Email How To, Email Security Best Practices, Two-Factor Authentication, Email Security Trends, Email Best Practices
Is your Mail Server Running Out of Disk Space?
By Brad Wyro posted in Email How To, Two-Factor Authentication, Email Security Trends, Email Best Practices