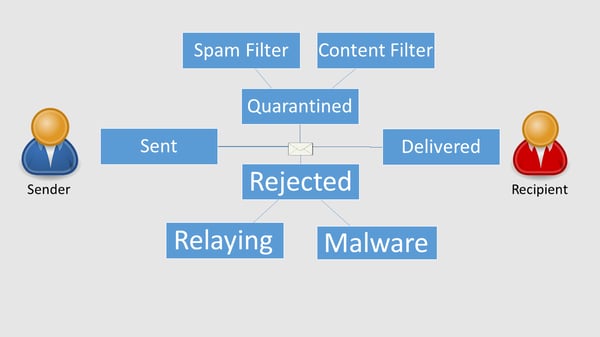
If you're in charge of managing your company's email, whether you're running an in-house Exchange server or Office 365, you've certainly become all too familiar with the latest threats posed by cybercriminals - threats that go far beyond the old-school Nigerian Prince email scam that has become the brunt of jokes over the past couple of decades. So if protecting your employees from email-borne scams is important to you & your business, a secure email gateway to protect against phishing, malware, data leaks and other threats would be a sound investment.

.png)