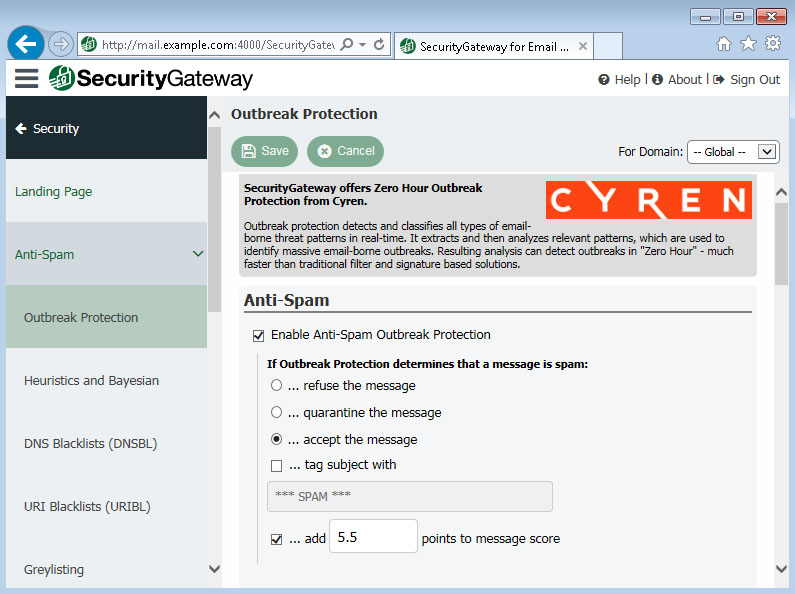
We live in an era where the amount of valuable data businesses must store is increasing at an unprecedented pace. Consequently, the number of cyber criminals trying to gain access to that data is also increasing. In fact, according to a report released last year by Osterman Research, 81% of organizations have been the victim of some type of data breach, targeted email attack, successful phishing attack or other cyber security incident during the previous 12 months. And with the surge of people working from home due to the COVID-19 pandemic, these numbers are only going to go up.